Microsoft Uncovers ‘Moonstone Sleet’ — New North Korean Hacker Group
A new North Korean threat actor, Moonstone Sleet, has surfaced, targeting individuals and organizations in sectors such as software and information technology, education, and the defense industrial base. This group employs a mix of ransomware and bespoke malware, showing tactical similarities with the notorious Lazarus Group, also known as Diamond Sleet. Moonstone Sleet uses various methods, including setting up fake companies and job opportunities, trojanizing legitimate tools, creating malicious games, and delivering custom ransomware. Initially tracked by Microsoft as Storm-1789, it has evolved a distinct identity, although it reuses code from known malware like Comebacker, which Lazarus has used in campaigns against security researchers. Attack methods include trojanized PuTTY applications, malicious npm packages, and a modified game called DeTankWar. The group also seeks legitimate employment to generate revenue or gain covert access to organizations. Recent attacks involve deploying custom ransomware, FakePenny, and creating fake companies for social engineering. These activities highlight the persistent threat posed by state-aligned North Korean cyber adversaries.
Overview of Moonstone Sleet’s Operations
Fake Companies and Job Opportunities
Moonstone Sleet targets individuals by creating fake companies and offering fraudulent job opportunities as a pretext to distribute trojanized tools, malicious games, and custom ransomware. This approach is part of a broader strategy that blends traditional attack techniques with novel methods. By masquerading as legitimate entities, the group successfully engages potential victims, facilitating the delivery of bespoke malware and ransomware. This tactic allows Moonstone Sleet to effectively infiltrate various sectors, including software, IT, education, and defense, leveraging both established and innovative cyber attack methodologies to achieve their strategic objectives.
Tactical Overlaps and Distinct Identity
Initially tracked by Microsoft as Storm-1789, Moonstone Sleet demonstrated strong tactical similarities with the Lazarus Group. Over time, it has developed a distinct identity through its own infrastructure and tradecraft. A notable overlap is the reuse of code from known malware like Comebacker, which was first observed in January 2021. Despite these similarities, Moonstone Sleet’s unique methods and tools distinguish it from Lazarus, showcasing its evolution into a separate, sophisticated threat actor.
Use of Comebacker Malware
The Lazarus Group has used the Comebacker malware in campaigns specifically targeting security researchers. This malware is often hidden within seemingly innocuous Python and npm packages. Once these packages are installed, Comebacker establishes contact with a command-and-control (C2) server to retrieve additional payloads. This method allows the attackers to maintain control over the compromised systems and deploy further malicious code as needed, making it a versatile and persistent threat in their cyber arsenal.
Attack Strategies and Techniques
Employment in Legitimate Companies
Moonstone Sleet seeks employment in legitimate software development positions, likely aiming to generate illicit revenue for North Korea or gain covert access to targeted organizations. By infiltrating these companies, the group can execute further attacks, steal sensitive data, and compromise systems from within, enhancing their operational capabilities and strategic objectives.
Modified PuTTY and Operation Dream Job
In August 2023, Moonstone Sleet employed a modified version of PuTTY, a tactic that the Lazarus Group had previously used in late 2022 during Operation Dream Job. The targets received a .ZIP archive containing a trojanized version of putty.exe and a file named url.txt. When the IP address and password provided in url.txt were entered into PuTTY, it decrypted and executed an embedded payload. This method allowed the attackers to deliver malicious code efficiently, continuing their campaign of sophisticated cyber attacks.
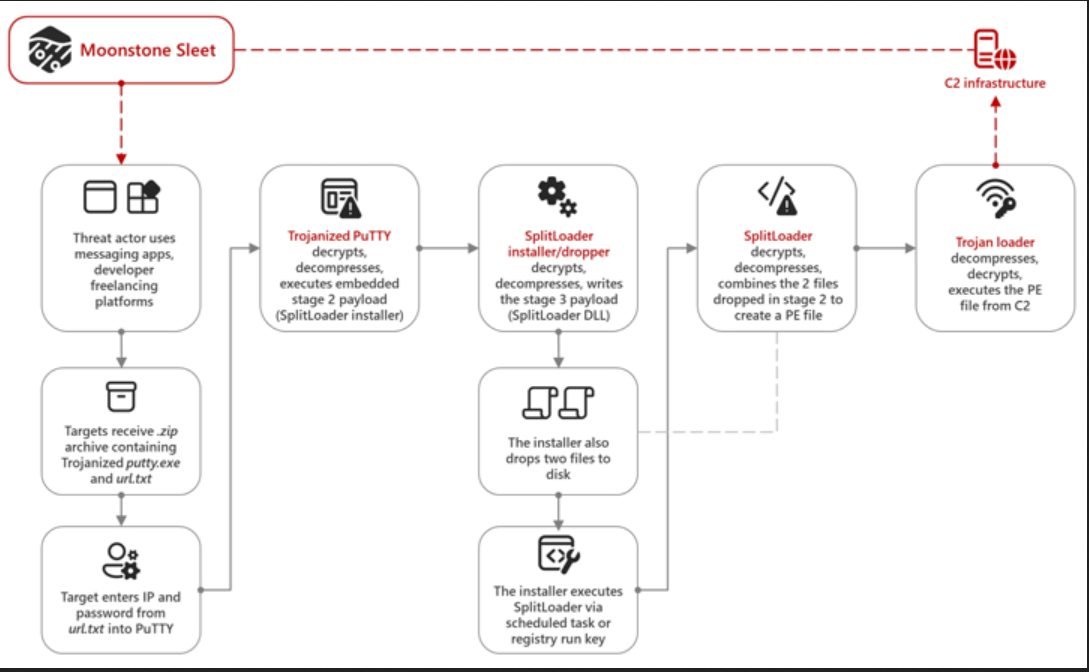
SplitLoader and Trojan Loader
The trojanized PuTTY executable drops a custom installer called SplitLoader. This initiates a sequence of intermediate stages to ultimately launch a Trojan loader, responsible for executing a portable executable from a C2 server.
Malicious npm Packages
Moonstone Sleet also uses malicious npm packages delivered through platforms like LinkedIn or freelancing websites. These packages connect to actor-controlled IP addresses, drop payloads similar to SplitLoader, or facilitate credential theft from the Windows Local Security Authority Subsystem Service (LSASS).
Other Attack Vectors
DeTankWar: A Malicious Game
Since February 2024, Moonstone Sleet has distributed a malicious game called DeTankWar via email or messaging platforms. The game comes with a malware loader, YouieLoad, capable of loading next-stage payloads and creating malicious services for network and user discovery, and browser data collection.
Fake Companies for Social Engineering
Moonstone Sleet creates fake companies such as C.C. Waterfall and StarGlow Ventures for social engineering campaigns. These entities masquerade as legitimate software development companies, reaching out to prospective targets for collaboration on various projects.
Ransomware Deployment
FakePenny Ransomware
In April 2024, Moonstone Sleet launched a custom ransomware variant named FakePenny against an unnamed defense technology company, demanding a $6.6 million Bitcoin ransom. This approach reflects tactics used by Andariel, a sub-group of the Lazarus Group known for deploying ransomware families such as H0lyGh0st and Maui. By employing similar ransomware strategies, Moonstone Sleet demonstrates its alignment with established North Korean cyber attack methods, further highlighting its role in state-sponsored cybercrime aimed at extorting significant financial gains from targeted organizations.
Security Recommendations
Defending Against Moonstone Sleet
Redmond advises software companies to implement robust security measures to defend against Moonstone Sleet’s attacks. Given North Korean hacking groups’ tendency to target the software supply chain, heightened vigilance is crucial. These groups often poison the supply chain to conduct widespread malicious operations, making it imperative for organizations to enhance their defenses, monitor for suspicious activity, and ensure their software integrity to prevent potential breaches.
Remediation Steps
- Implement Multi-Factor Authentication (MFA): Ensure all user accounts, especially those with privileged access, require MFA to enhance security.
- Regularly Update Software: Keep all software, including operating systems and applications, up to date with the latest security patches to prevent exploitation of known vulnerabilities.
- Conduct Security Awareness Training: Educate employees about phishing attacks, social engineering, and safe browsing practices to reduce the risk of falling for fake job offers or malicious links.
- Monitor Network Traffic: Use intrusion detection and prevention systems (IDPS) to monitor network traffic for unusual activity and potential indicators of compromise (IoCs).
- Isolate Suspected Infections: Implement network segmentation and establish protocols to quickly isolate and remediate suspected infections to prevent lateral movement.
- Regular Backups: Maintain regular, encrypted backups of critical data and ensure they are stored offline to mitigate the impact of ransomware attacks.
- Audit and Limit Access: Conduct regular audits of user permissions and limit access to sensitive data and systems based on the principle of least privilege



