Mysterious Cyber Attack Took Down 600,000+ Routers in the U.S.
Between October 25 and October 27, 2023, an unidentified cyber-attack targeted over 600,000 small office/home office (SOHO) routers, rendering them inoperable and disrupting users’ internet access and other computer resources. The attack primarily impacted three router models: ActionTec3200, Action Tec T3260, and Sagemcom. The assailants utilized the Remote Access Trojan named Chalubo to exacerbate the chaos, prolonging recovery efforts. This 72-hour incident highlighted the vulnerability of SOHO router systems and the potential for widespread disruption caused by cyber threats. Users were left grappling with the aftermath, facing significant downtime and compromised connectivity. The scale and duration of the attack underscored the need for robust cybersecurity measures to safeguard critical infrastructure and prevent similar incidents in the future. Efforts to restore affected routers and mitigate the damage were met with significant challenges, further emphasizing the sophistication and impact of the attack. The incident served as a wake-up call for organizations and individuals alike, highlighting the importance of proactive security measures and vigilance against evolving cyber threats. The disruption caused by the attack reverberated across various sectors, underscoring the interconnected nature of today’s digital landscape and the cascading effects of cyber-attacks on global networks. Despite efforts to identify the perpetrators, their identity remained elusive, raising concerns about the motives behind the attack and the potential for future breaches. The widespread nature of the attack and its targeting of essential networking equipment highlighted the critical role of routers in maintaining internet connectivity and facilitating communication in modern society. The incident prompted calls for greater collaboration among cybersecurity professionals, government agencies, and technology companies to address vulnerabilities and enhance resilience against cyber threats. In the aftermath of the attack, affected users and organizations scrambled to bolster their defenses and implement remediation measures to prevent similar incidents from occurring in the future. The lasting impact of the attack served as a stark reminder of the ever-present threat posed by malicious actors in the digital realm and the imperative for continuous innovation in cybersecurity practices and technologies.
ATTACK OVERVIEW:
“The incident took place over a 72-hour period between October 25-27, rendered the infected devices permanently inoperable, and required a hardware-based replacement,” the company said in a technical report. The mysterious event, which took place between October 25 and 27, 2023, and impacted a single internet service provider (ISP) in the U.S., has been codenamed Pumpkin Eclipse by the Lumen Technologies Black Lotus Labs team. It specifically affected three router models issued by the ISP: ActionTec T3200, ActionTec T3260, and Sagemcom. The blackout is significant, not least because it led to the abrupt removal of 49% of all modems from the impacted ISP’s autonomous system number (ASN) during the time-frame.
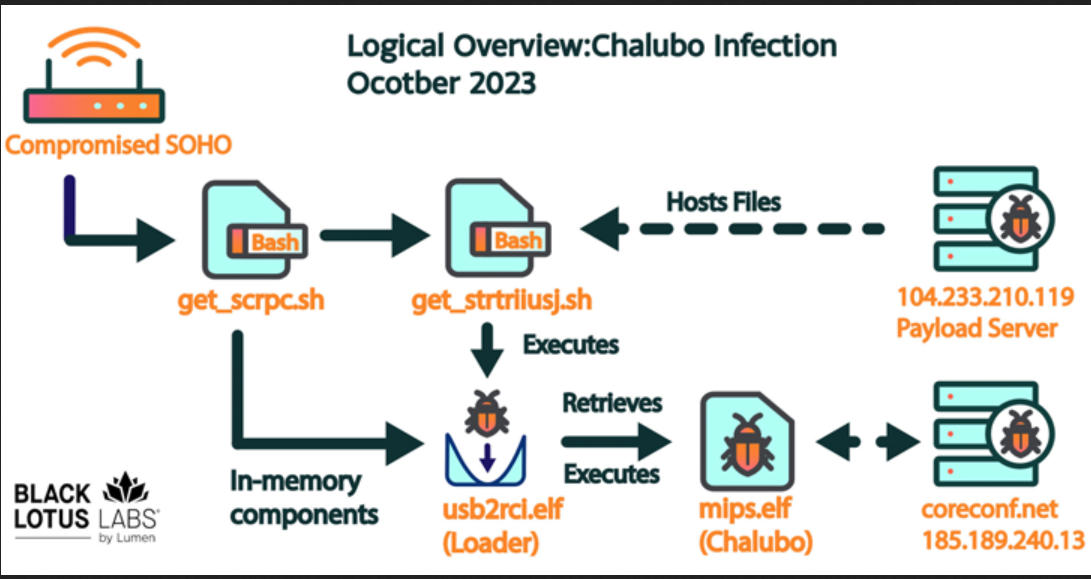
THE REMOTE ACCESS TROJAN (RAT):
Chalubo: It is a stealthy malware first documented by Sophos in October 2018 – as responsible for the sabotage, with the adversary opting for it presumably in an effort to complicate attribution efforts rather than use a custom toolkit.
“Chalubo has payloads designed for all major SOHO/IoT kernels, pre-built functionality to perform DDoS attacks, and can execute any Lua script sent to the bot,” the company said. “We suspect the Lua functionality was likely employed by the malicious actor to retrieve the destructive payload.”
Upon gaining a successful foothold, the infection chain proceeds to drop shell scripts that pave the way for a loader ultimately designed to retrieve and launch Chalubo from an external server. The destructive Lua script module fetched by the Trojan is unknown.
Only one panel was used during the disruptive attack and not all Chalubo infections participated in it, suggesting that the panel might have been purchased to hinder attribution.
“This suggests that while the Chalubo malware was used in this destructive attack, it was not written specifically for destructive actions. We suspect the threat actors behind this event chose a commodity malware family to obfuscate attribution, instead of using a custom-developed toolkit,” Lumen says.
THE ATTACK (CHALUBO):
SophosLabs first discovered the Chalubo family from an attack on one of our honeypots, which we use to collect data on malicious activity. We recorded the attack on the 6th of September 2018 with the bot attempting to brute force login credentials against an SSH server; our honeypots present the attacker with the appearance of a real shell that accepts a wide range of credentials. The attackers used the combination of rood:admin to gain a shell.
THE NOTABLE ASPECT OF THE CAMPAIGN:
A notable aspect of the campaign is its targeting of a single ASN, as opposed to others that have typically targeted a specific router model or common vulnerability, raising the possibility that it was deliberately targeted, although the motivations or intentions behind it are undetermined as yet.
“The event was unprecedented due to the number of units affected – no attack that we can recall has required the replacement of over 600,000 devices,” Lumen said. “In addition, this type of attack has only ever happened once before, with AcidRain used as a precursor to an active military invasion.”
REMEDIATION STEPS:
- Keep Firmware Updated: Regularly check for firmware updates provided by your router manufacturer and promptly install them. These updates often include security patches that address known vulnerabilities and enhance the router’s overall performance and stability. When shopping for a router, choose a brand that takes security seriously and offers firmware updates for security issues discovered throughout the product’s lifetime.
- Change Default Credentials: One of the most common router security oversights by end-users is neglecting to change the default login credentials (username and password) for your router’s administrative interface. Replace these default credentials and weak passwords with unique, strong passwords to prevent unwanted remote connections to your device as weak and easy passwords can give the attacker easy access to your device.
- Enable Strong WiFi Encryption: Ensure that your router’s WiFi network is encrypted using a robust WiFi security protocol such as WPA2 or WPA3. For more information learn more on how to set WPA3 on your router. Use a strong passphrase for the Wi-Fi password, comprising a combination of uppercase and lowercase letters, numbers, and special characters.
- Disable Remote Management: Disable remote management features on your router unless absolutely necessary. Remote management functionality can potentially expose your router to remote exploitation, increasing the risk of unauthorized access. A strong password can help reduce the risks of remote management.
- Implement Network Segmentation: Segment your network into separate subnets for different devices or user groups. This practice prevents hackers from moving between different parts of a network, reducing the impact of a security breach. Make sure you have a guest network for visitors or for IoT devices that you don’t fully trust.
- Choose a router with built-in security: Some routers such as the Nighthawk and Orbi series ship with built-in cyber-security protection to detect and block attacks against devices that are part of the local network. This technology also ensures that local devices are scanned for vulnerabilities so you can get an overview of your network’s security. By implementing these proactive measures and staying informed about emerging threats, you can bolster the security of your router and safeguard your network against ever-increasing modern cyber-attacks. Remember, protecting your router is not just about securing your internet connection —it’s about safeguarding your digital livelihood and ensuring peace of mind in an increasingly connected world.



