Rebranded Knight Ransomware Targeting Healthcare and Businesses Worldwide
RansomHub, a newly emerged ransomware strain, has been identified as an updated and rebranded version of Knight ransomware, which evolved from Cyclops ransomware. This blog explores the technical details, operational tactics, and recent developments of RansomHub. Originally, Cyclops laid the foundation for this ransomware lineage with robust encryption and data extortion tactics. Knight ransomware, arriving in May 2023, utilized double extortion across multiple platforms, including Windows, Linux, macOS, ESXi, and Android. Advertised on the RAMP cybercrime forum, Knight spread through phishing campaigns. The RaaS operation behind Knight shut down in February 2024, with its source code sold, likely leading to the creation of RansomHub. RansomHub launched attacks on Change Healthcare, Christie’s, and Frontier Communications, while avoiding targets in CIS countries, Cuba, North Korea, and China. Both Knight and RansomHub are written in Go and use Gobfuscate for obfuscation, sharing significant code overlap, with RansomHub adding a “sleep” option. Their obfuscation techniques, ransom notes, and safe mode capabilities are similar, differing mainly in command execution via cmd.exe. RansomHub exploits known security flaws like ZeroLogon, deploying remote desktop software before ransomware. In April 2024, RansomHub was linked to 26 attacks. Mandiant reported RansomHub recruiting affiliates from recent RaaS shutdowns, including former Noberus affiliates. 2023 saw a rise in ransomware activity with many new strains being rebrands, highlighting code reuse. Ransomware deployment often occurred within 48 hours of access, mainly outside work hours, using legitimate tools to evade detection. New variants like BlackSuit and ShrinkLocker continue to emerge, demonstrating sophisticated tactics. Understanding these developments is crucial for strengthening cybersecurity defenses.
Evolution from Cyclops to RansomHub
Cyclops: The Beginning
Cyclops ransomware, the first strain in its lineage, distinguished itself with powerful encryption methods and aggressive data extortion tactics. By setting a high standard in these areas, Cyclops paved the way for the development of its successor, Knight ransomware. This original strain’s capabilities laid the critical groundwork, influencing the more advanced techniques and strategies seen in Knight ransomware. Through its pioneering approach, Cyclops played a crucial role in shaping the evolution of ransomware tactics, demonstrating a sophisticated blend of encryption and extortion that would be refined and enhanced in subsequent versions.
Knight Ransomware: Cyclops 2.0
Arriving in May 2023, Knight ransomware, also referred to as Cyclops 2.0, marked its entry by employing double extortion tactics. This involved not only encrypting victims’ data but also stealing it to leverage ransom demands. Knight ransomware targeted a broad range of platforms, including Windows, Linux, macOS, ESXi, and Android, showcasing its versatility and widespread threat. It gained significant attention and promotion on the RAMP cybercrime forum, becoming a notable presence in the cybercriminal landscape. Its distribution methods were primarily through phishing and spear-phishing campaigns, which used malicious attachments to infect victims. This strategic approach allowed Knight to effectively infiltrate and compromise various systems, making it a formidable successor to Cyclops ransomware. Through its advanced techniques and extensive reach, Knight ransomware underscored the evolving nature of cyber threats in 2023.
Transition to RansomHub
Shutdown and Source Code Sale
By the end of February 2024, the ransomware-as-a-service (RaaS) operation supporting Knight ceased its activities, and the source code was traded. This significant occurrence hinted at a transition in ownership to a different entity, which subsequently rebranded and improved the ransomware, now referred to as RansomHub.
Launch and Initial Attacks
Since its emergence in February 2024, RansomHub has embarked on a menacing spree, leaving a trail of disruption and chaos in its wake. With its first victim posted in that fateful month, this nefarious strain of ransomware has shown no signs of relenting, launching relentless attacks on prominent entities like Change Healthcare, Christie’s, and Frontier Communications. Despite the havoc it has wrought, RansomHub has made a chilling declaration: it will abstain from targeting entities within the Commonwealth of Independent States (CIS) countries, Cuba, North Korea, and China. This selective approach to its targets adds a layer of complexity to its motives, raising questions about the underlying agenda of its creators. As cybersecurity experts grapple with the challenge of mitigating its impact, the specter of RansomHub continues to loom large, underscoring the urgent need for robust defenses and international cooperation to combat such malicious threats effectively.
Technical Analysis
Code Overlap and Obfuscation
Knight and RansomHub, both constructed using Go and employing Gobfuscate for obfuscation, present a formidable challenge for differentiation, as noted in Symantec’s report. The study underscores a substantial degree of code overlap between these two malicious entities, complicating efforts to distinguish between them. Notably, they share identical command-line help menus, a striking similarity that blurs the lines between their operational frameworks. However, RansomHub introduces a notable variation with its inclusion of a “sleep” option, a tactic reminiscent of strategies observed in other ransomware families such as Chaos/Yashma and Trigona. This convergence of tactics across various ransomware strains highlights a concerning trend in the evolution of cyber threats, where adversaries borrow and adapt techniques from one another to enhance their malicious capabilities. As cybersecurity experts strive to stay ahead of these developments, the need for innovative detection and mitigation strategies becomes increasingly imperative to safeguard against such insidious attacks effectively.
Shared and Unique Features
- String Obfuscation: Both ransomware families use similar techniques to encode strings.
- Ransom Notes and Safe Mode: They drop almost identical ransom notes and can restart a host in safe mode before encryption.
- Command Execution: The primary difference lies in the specific commands executed via cmd.exe, though the sequence and context of their execution remain the same.
Attack Vectors and Tactics
Distribution Methods
RansomHub exploits known security vulnerabilities, like ZeroLogon, for initial access and deploys remote desktop software such as Atera and Splashtop before initiating ransomware deployment, echoing the tactics employed by Knight ransomware. This strategic approach underscores RansomHub’s adeptness at leveraging established security weaknesses and familiar attack vectors to infiltrate target systems, highlighting the sophistication of its operational methodology. As RansomHub continues to refine its techniques and expand its arsenal, the imperative for robust cybersecurity measures becomes increasingly paramount to thwart its malicious activities effectively.
Recent Attack Statistics
During April 2024, RansomHub’s involvement was confirmed in 26 separate attacks, positioning it among significant players such as Play, Hunters International, Black Basta, and LockBit. This surge in activity underscores RansomHub’s escalating impact within the ransomware landscape, solidifying its position as a formidable threat alongside established adversaries. As the tally of its victims continues to rise, the urgency to address and neutralize RansomHub’s operations intensifies, necessitating concerted efforts from cybersecurity experts and affected organizations to mitigate its damaging effects effectively.
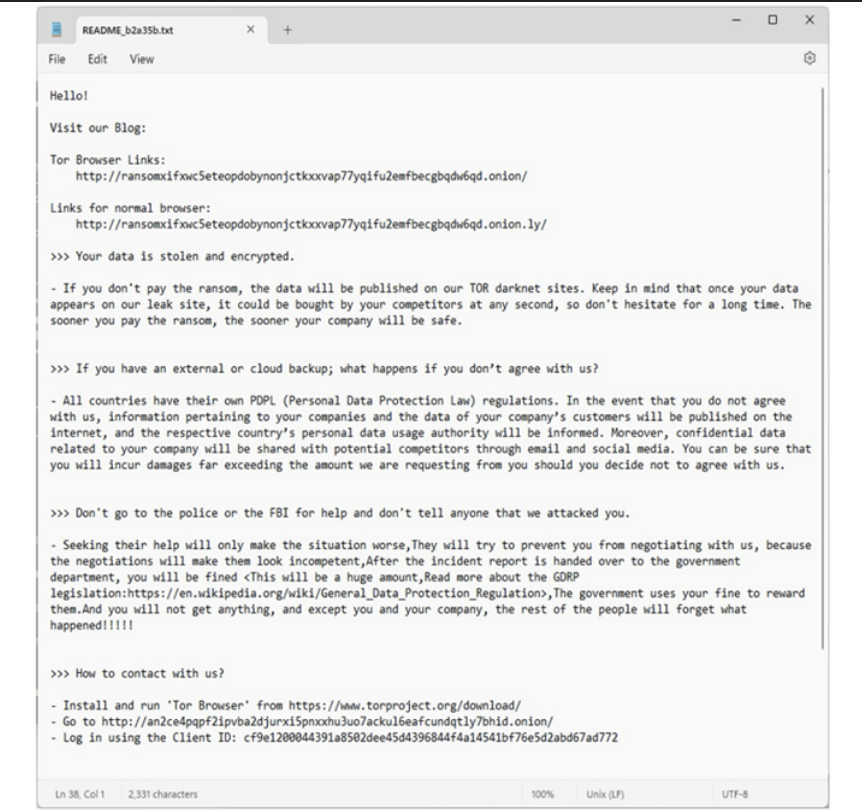
Affiliate Recruitment and Tools
According to security researcher, RansomHub, under Google’s ownership, is actively seeking affiliates impacted by recent Ransomware-as-a-Service (RaaS) closures or exit scams like LockBit and BlackCat. Noteworthy is the involvement of former Noberus affiliate “Notchy” and tools attributed to another affiliate, “Scattered Spider,” in recent RansomHub operations. This recruitment strategy highlights RansomHub’s efforts to capitalize on the fallout from RaaS disruptions, reinforcing its presence in the ransomware ecosystem while leveraging the expertise and resources of experienced affiliates. As these affiliations underscore, RansomHub poses a significant and evolving threat, necessitating continuous monitoring and robust countermeasures to mitigate its impact effectively.
Ransomware Trends and Future Outlook
Increasing Activity and Code Reuse
In 2023, the threat landscape witnessed a resurgence in ransomware activity, marking a notable uptick following a brief decline observed in 2022. Of the 50 new ransomware families documented during this period, approximately one-third emerged as variants of previously identified strains, shedding light on the pervasive trend of code recycling and rebranding within the cybercriminal community. This prevalence of repurposed code underscores the adaptability and persistence of malicious actors, who continuously seek to revitalize their campaigns through iterative modifications and reiterations of existing malware frameworks. The phenomenon highlights the dynamic nature of the cybersecurity landscape, where adversaries leverage past successes and exploit vulnerabilities to perpetuate their nefarious agendas. As organizations and security experts grapple with this evolving threat landscape, the imperative to bolster defenses and implement proactive measures against ransomware attacks becomes increasingly pressing to mitigate risks and safeguard critical assets effectively.
Attack Characteristics
- Deployment Speed: Ransomware was deployed within 48 hours of initial access in almost one-third of incidents.
- Timing: 76% of deployments occurred outside work hours, mainly in the early morning.
- Tool Usage: Attackers increasingly rely on legitimate remote desktop tools to conceal operations and reduce the need for custom tools.
Emergence of New Variants
The emergence of novel ransomware variants such as BlackSuit, Fog, and ShrinkLocker signifies a dynamic shift in cyber threat tactics. Each variant brings distinctive strategies to the forefront: ShrinkLocker, for instance, showcases its sophistication by employing VBScript and Windows utilities to leverage Microsoft’s BitLocker for file encryption, showcasing an intricate grasp of Windows internals. This demonstrates a concerning level of ingenuity and adaptability among cybercriminals, who continually explore new avenues to evade detection and maximize the impact of their attacks. As these malicious actors evolve, the cybersecurity landscape demands heightened vigilance and proactive defense measures to counter emerging threats effectively. Organizations must remain agile in their response strategies, leveraging advanced threat intelligence and robust security frameworks to mitigate the risks posed by these evolving ransomware variants.
Remediation Steps
- Patch Management: Regularly update and patch all software and systems to close known vulnerabilities.
- Employee Training: Conduct ongoing security awareness training to recognize and avoid phishing and spear-phishing attacks.
- Multi-Factor Authentication (MFA): Implement MFA to add an additional layer of security for all remote access points.
- Network Segmentation: Segment networks to limit the spread of ransomware and restrict access to sensitive data.
- Backup and Recovery: Maintain regular, secure backups of critical data and test recovery processes frequently.
- Endpoint Protection: Deploy and maintain comprehensive endpoint detection and response (EDR) solutions to detect and mitigate threats in real time.
- Incident Response Plan: Develop and regularly update an incident response plan, including communication strategies and roles during a ransomware attack.



