Unveiling the Latest More_eggs Malware Phishing Attack
In May 2024, cybersecurity researchers from eSentire uncovered an attempted phishing attack aimed at an unnamed company in the industrial services industry. The attack utilized the More_eggs malware, cleverly disguised as a resume to deceive a recruiter into downloading it. This tactic, while not novel, highlights the persistent and ever-evolving strategies employed by cybercriminals to infiltrate organizations. The attackers crafted a sophisticated social engineering scheme, posing as job applicants and providing a link to a purported resume download site. Once the recruiter followed the link, they unknowingly downloaded a malicious Windows Shortcut file (LNK), which then facilitated the retrieval of a harmful DLL through the legitimate Microsoft program ie4uinit.exe. This DLL was subsequently executed using regsvr32.exe, allowing the malware to establish persistence, collect data about the infected host, and deploy additional payloads, including the More_eggs backdoor. Notably, when the same URL was visited later, it displayed only a plain HTML resume, leaving no trace of the malware, thereby avoiding detection and reducing suspicion. This incident underscores the sophistication of modern phishing attacks and the need for robust cybersecurity measures. It also emphasizes the importance of continuous employee training to recognize and report suspicious activities, particularly in recruitment processes where social engineering tactics are commonly employed. The ongoing activity of More_eggs campaigns, despite their initial detection over two years ago, reflects the adaptability and resilience of cyber threats, reinforcing the necessity for advanced defensive strategies to protect sensitive information and maintain organizational security.
The More_eggs Malware and Golden Chickens
More_eggs, a sophisticated modular backdoor malware, is attributed to the notorious cybercriminal group known as Golden Chickens (also referred to as Venom Spider). This malware is particularly insidious due to its distribution model, Malware-as-a-Service (MaaS). Through MaaS, Golden Chickens offer More_eggs to other cybercriminal actors, enabling a wide range of malicious activities. Primarily, More_eggs is employed to harvest sensitive information from infected systems, making it a valuable tool for cyber espionage, data theft, and other nefarious purposes. The modular nature of More_eggs allows it to be highly adaptable and customizable, enhancing its effectiveness across various targets and environments. This flexibility ensures that the malware can persist and operate undetected within compromised networks, continuously evolving to bypass security measures. The MaaS model also democratizes access to this potent malware, increasing its proliferation and the overall threat landscape. Consequently, More_eggs remains a significant concern for cybersecurity professionals, who must stay vigilant and employ advanced defense mechanisms to protect against such sophisticated threats. By understanding the operational methods and distribution strategies of More_eggs, organizations can better prepare and fortify their defenses against potential intrusions and data breaches.
Attack Vector and Methodology
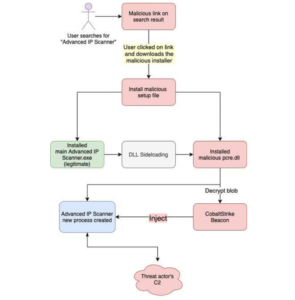
LinkedIn-Based Phishing Tactic
The recent attack involved malicious actors responding to LinkedIn job postings with a link to a fake resume download site. Here’s a step-by-step breakdown of the attack chain:
- Initial Contact: The targeted recruiter received a response to their job posting, which included a link to a purported resume download site.
- Malicious Download: Following the link led to the download of a malicious Windows Shortcut file (LNK).
- Payload Delivery: The LNK file was used to retrieve a malicious DLL via the legitimate Microsoft program ie4uinit.exe.
- Persistence and Execution: The retrieved DLL was executed using regsvr32.exe, establishing persistence, gathering host data, and dropping additional payloads, including the More_eggs backdoor.
Social Engineering Tactics
The attack used social engineering by posing as job applicants to deceive recruiters. Initially, recruiters were directed to a download site where they downloaded a malicious file, thinking it was a resume. Interestingly, subsequent visits to the same URL displayed only a plain HTML resume, with no trace of the malware. This tactic effectively evades detection and reduces suspicion, making it harder for security measures to identify and block the threat. By blending in with legitimate activities, the attackers increase their chances of successfully compromising targeted systems without raising immediate alarms.
Continued Activity and Techniques
More_eggs Campaigns
Despite being detected over two years ago, More_eggs campaigns continue to be active and pose a significant threat. These campaigns selectively target individuals using sophisticated social engineering tactics. Unlike typical malspam distribution networks, the use of Malware-as-a-Service (MaaS) offerings in More_eggs campaigns is sparse and highly selective. This strategic approach enables the attackers to focus on high-value targets, enhancing the effectiveness of their operations. The persistence of More_eggs highlights the evolving nature of cyber threats and the importance of robust cybersecurity measures to detect and mitigate these targeted attacks.
Drive-by Download Campaign
In a related development, eSentire identified a drive-by download campaign leveraging fake websites for the KMSPico Windows activator tool to distribute the Vidar infostealer. The kmspico[.]ws site, hosted behind Cloudflare Turnstile, employed a unique tactic requiring human input to download a final ZIP package. This approach effectively evaded automated web crawlers, making the malicious payload more difficult to detect. By mimicking a legitimate software activation tool, the campaign deceived users into initiating the download, subsequently infecting their systems with Vidar. This infostealer is designed to harvest sensitive data, including credentials and financial information, highlighting the need for vigilance and advanced security measures to combat such sophisticated threats.
Emergence of Phishing Kit V3B
Another significant development is the emergence of the V3B phishing kit, which has been active since March 2023. This kit specifically targets banking customers in the European Union and supports over 54 banks. It operates under a Phishing-as-a-Service (PhaaS) model, making it accessible to a wide range of cybercriminals. Key features of V3B include customized and localized templates that mimic various online banking and e-commerce authentication processes, enhancing its deceptive capabilities. The kit allows real-time interaction with victims to capture credentials and one-time passwords (OTPs), and it can execute QR code login jacking (QRLJacking) attacks, particularly on services like WhatsApp. These advanced capabilities, combined with its ease of use, have made V3B a popular tool among cybercriminals, significantly increasing the risk of fraud and unauthorized access to financial accounts across Europe.
- Customized and localized templates for various online banking and e-commerce systems.
- Real-time interaction with victims to capture credentials and one-time passwords (OTPs).
- Execution of QR code login jacking (QRLJacking) attacks, particularly on services like WhatsApp.
Remediation Steps for More_eggs Malware Attacks
- Educate and Train Employees: Conduct regular cybersecurity awareness training, emphasizing the dangers of phishing attacks and safe email practices.
- Implement Email Filtering: Use advanced email filtering solutions to detect and block phishing emails and malicious attachments.
- Use Endpoint Protection: Deploy robust endpoint protection solutions to detect and prevent the execution of malicious files.
- Monitor Network Traffic: Continuously monitor network traffic for unusual activity and potential indicators of compromise.
- Regular Software Updates: Ensure all systems and software are regularly updated with the latest security patches to close vulnerabilities.
- Restrict Download Permissions: Limit the ability of users to download and execute files from unknown or untrusted sources.
- Backup and Recovery Plan: Maintain regular backups of critical data and have a tested incident response and recovery plan in place.



