China-Linked ValleyRAT Malware Resurfaces with Advanced Data Theft Tactics
Cybersecurity researchers have identified an updated version of the ValleyRAT malware, which is now being disseminated as part of a new campaign. According to security researchers , the latest iteration of ValleyRAT has introduced several new commands, including the ability to capture screenshots, filter processes, force shutdowns, and clear Windows event logs. ValleyRAT was previously documented by QiAnXin and Proofpoint in 2023 in association with a phishing campaign targeting Chinese-speaking users and Japanese organizations. This campaign distributed various malware families, including Purple Fox and a variant of the Gh0st RAT Trojan known as Sainbox RAT or FatalRAT. The inclusion of new capabilities in ValleyRAT signifies a significant evolution in its functionality, making it a more potent threat to targeted systems. The ongoing development and deployment of such sophisticated malware underscore the persistent and evolving nature of cyber threats, highlighting the need for robust cybersecurity measures to protect against these advanced attacks. This discovery serves as a stark reminder of the importance of staying vigilant and informed about the latest threats in the cybersecurity landscape.
ATTACK OVERVIEW:
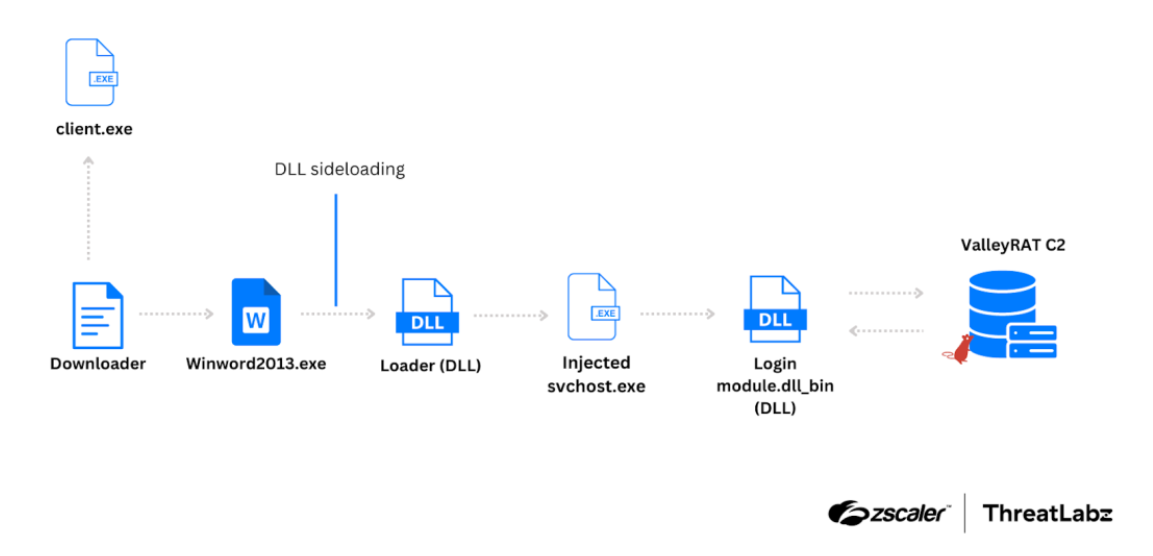
The malware has been assessed to be the work of a China-based threat actor, boasting of capabilities to harvest sensitive information and drop additional payloads onto compromised hosts. The starting point is a downloader that utilizes an HTTP File Server (HFS) to fetch a file named “NTUSER.DXM” that’s decoded to extract a DLL file responsible for downloading “client.exe” from the same server. The decrypted DLL is also designed to detect and terminate anti-malware solutions from Qihoo 360 and WinRAR in an effort to evade analysis, after which the downloader proceeds to retrieve three more files – “WINWORD2013.EXE,” “wwlib.dll,” and “xig.ppt” – from the HFS server. Next, the malware launches “WINWORD2013.EXE,” a proper legitimate executable associated with Microsoft Word, using it to sideload “wwlib.dll” that, in turn, establishes persistence on the system and loads “xig.ppt” into memory. “From here, the decrypted ‘xig.ppt’ continues the execution process as a mechanism to decrypt and inject shellcode into svchost.exe,” the researchers said. “The malware creates svchost.exe as a suspended process, allocates memory within the process, and writes shellcode there.” The shellcode, for its part, contains necessary configuration to contact a command-and-control (C2) server and download the ValleyRAT payload in the form of a DLL file.
SAINBOX RAT (A VARIANT OF GH0ST TROJAN):
SainboxRAT or FatalRAT is the name of a Remote Access Trojan (RAT). A RAT is a type of malware that allows the attacker to remotely control the infected computer and use it for various purposes. Typically, RATs are used to access files and other data, watch computing activities on the screen and capture screenshots, steal sensitive information (e.g., login credentials, credit card details). There are many legitimate remote administration/access tools on the Internet. It is common that cybercriminals use those tools with malicious intent too and for accessing the user’s computer for malicious purposes.
AGENT TESLA:
Agent Tesla is a .Net-based Remote Access Trojan (RAT) and data stealer for gaining initial access that is often used for Malware-As-A-Service (MaaS). In this criminal business model, threat actors known as initial access brokers (IAB) outsource their specialized skills for exploiting corporate networks to affiliate criminal groups. As first-stage malware, Agent Tesla provides remote access to a compromised system that is then used to download more sophisticated second-stage tools, including ransomware.
Agent Tesla first appeared in 2014 and surged in the 2020s when it was leveraged for COVID-19 PPE-themed phishing campaigns. Agent Tesla delivers emails attached with .zip, .gz, .cab, .msi and .img files and Microsoft Office documents with malicious Visual Basic Application (VBA) macros to compromise victim systems. Agent Tesla phishing campaigns are notorious for precisely replicating a legitimate company’s communication tone and visual template, including logos and fonts. The development also comes as the Fortinet FortiGuard Labs uncovered a phishing campaign that targets Spanish-speaking people with an updated version of this keylogger and information stealer.
THE ILLEGAL ADVANTAGE OF MICROSOFT EXCEL ADD-INS (XLA) FILES:
The attack chain takes advantage of Microsoft Excel Add-Ins (XLA) file attachments that exploit known security flaws (CVE-2017-0199 and CVE-2017-11882) to trigger the execution of JavaScript code that loads a PowerShell script, which is engineered to launch a loader in order to retrieve Agent Tesla from a remote server.
“This variant collects credentials and email contacts from the victim’s device, the software from which it collects the data, and the basic information of the victim’s device,” security researcher Xiaopeng Zhang said. “Agent Tesla can also collect the victim’s email contacts if they use Thunderbird as their email client.” This can lead to proper exploitation of victim’s personal information and can be vulnerable to his email contacts.
REMEDIATION STEPS:
- Security Training: A RAT defense strategy is reliant on organization-wide security awareness training. Human error is the fundamental cause of most security events, and RAT is no exception. Attackers typically execute this malware via infected attachments and links in phishing campaigns. Employees must be vigilant, so they don’t unintentionally infect the company network.
- Strict Access Control Procedures: RATs are commonly used to compromise administrative credentials, providing attackers access to valuable data on the organization’s network. With tight access controls, you can restrict the fallout from compromised credentials. Stricter controls involve implementing two-step verification, stricter firewall configurations, whitelisting IP addresses for authorized users, and using more advanced antivirus solutions.
- Secure Remote Access Solutions: Attackers view each new endpoint that connects to your network as a potential system to compromise using RAT. Organizations should only allow remote access via secure connections created with virtual private networks (VPNs) or hardened, secure gateways to minimize the attack surface. In addition, you can use a clientless remote access solution that does not need additional plugins or software on end-user devices as these devices are targets for attackers.
- Zero-Trust Security Technologies: Zero-trustsecurity models have grown in popularity because they promote “never trust, always verify.” Instead of granting administrative credentials for complete access across the network, the zero-trust security approach grants granular control over lateral movements. This is critical to mitigating RAT attacks, because attackers use lateral movements to infect additional systems and access sensitive data.
- Focus on Infection Vectors: RATs, like all malware, are only a threatif they are installed and implemented on a target computer. Using secure browsing and anti-phishing solutions and consistently patching systems can minimize the likelihood of RATs. These solutions make it harder for RATs to infect a computer to begin with.
- Look for Abnormal Behavior: RATs are Trojans that can present as legitimate applications. RATs typically comprise malicious functionality connected to a real application. Monitor applications and systems for unusual behavior that may indicate a RAT.



