New Phishing Campaign Deploys WARMCOOKIE Backdoor Targeting Job Seekers
Cybersecurity researchers have disclosed details of an ongoing phishing campaign that has recruiting- and job-themed lures to deliver a Windows-based backdoor named WARMCOOKIE. “WARMCOOKIE appears to be an initial backdoor tool used to search out victim networks and deploy additional payloads,” Elastic Security Labs researcher Daniel Stepanic said in a new analysis. “Each sample is compiled with a hard-coded [command-and-control] IP address and RC4 key.” The backdoor comes with capabilities to fingerprint infected machines, capture screenshots, and drop more malicious programs. The company is tracking the activity under the name REF6127. The attack chains observed since late April involve the use of email messages purporting to be from recruitment firms like Hays, Michael Page, and PageGroup, urging recipients to click on an embedded link to view details about a job opportunity.
ATTACK OVERVIEW:
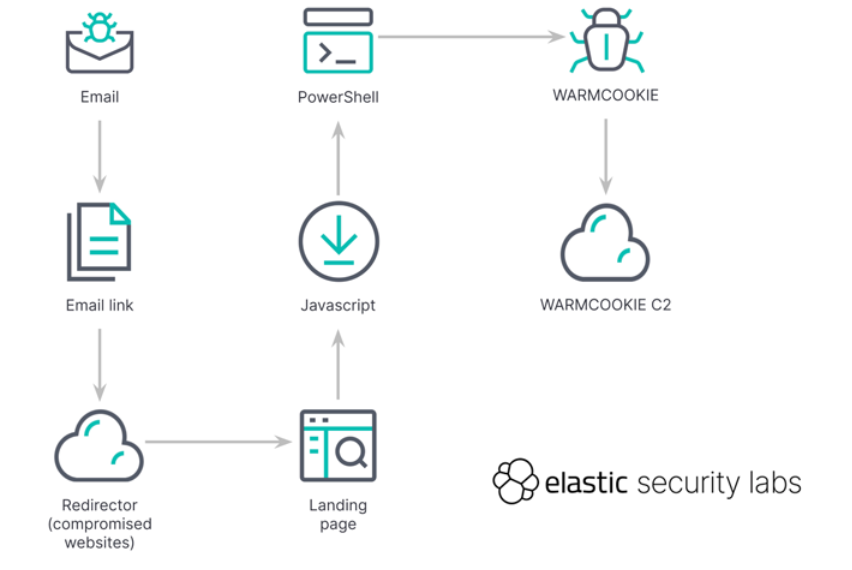
Users who end up clicking on the link are then prompted to download a document by solving a CAPTCHA challenge, following which a JavaScript file (“Update_23_04_2024_5689382.js”) is dropped. “This obfuscated script runs PowerShell, kicking off the first task to load WARMCOOKIE,” Elastic said. “The PowerShell script abuses the Background Intelligent Transfer Service (BITS) to download WARMCOOKIE.” A crucial component of the campaign is the use of compromised infrastructure to host the initial phishing URL, which is then used to redirect victims to the appropriate landing page. A Windows DLL, WARMCOOKIE follows a two-step process that allows for establishing persistence using a scheduled task and launching the core functionality, but not before performing a series of anti-analysis checks to sidestep detection. The backdoor is designed to capture information about the infected host in a manner that’s similar to an artifact used in connection with a previous campaign codenamed Resident that targeted manufacturing, commercial, and healthcare organizations.
“WARMCOOKIE” BACKDOOR:
WARMCOOKIE is a newly discovered backdoor used to fingerprint a machine, capture screenshots of the victim machine, and deploy additional payloads. Threat actors are spinning up new domains and infrastructure weekly to support these campaigns. This research includes an IDAPython script to decrypt strings from WARMCOOKIE. Elastic Security provides prevention and visibility capabilities across the entire WARMCOOKIE infection chain. It also supports commands to read from and write to files, execute commands using cmd.exe, fetch the list of installed applications, and grab screenshots. “WARMCOOKIE is a newly discovered backdoor that is gaining popularity and is being used in campaigns targeting users across the globe,” Elastic said. The disclosure comes as Trustwave SpiderLabs detailed a sophisticated phishing campaign that employs invoice-related decoys and takes advantage of the Windows search functionality embedded in HTML code to deploy malware.
WINDOWS “SEARCH”- URI PROTOCOL HANDLER:
The search: application protocol is an extensible convention for calling the desktop search application on Windows Vista with Service Pack 1 (SP1) and later versions. The protocol was created in Windows Vista with SP1 to give Windows a way to determine and call the default desktop search application. The protocol syntax provides a number of parameters useful for performing common desktop searches, such as user-entered search terms or the location on which the search was begun. When users search from one of the two available search entry points (either the Start menu or Windows Explorer), the operating system uses the search protocol to launch the default desktop search application. It does this by adding the user-entered search terms to the standard search protocol syntax and passing that information to the application registered as the default search application. If no other desktop search applications are installed, a search entered into these entry points launches the Windows Search Explorer. However, third-party developers can create, install, and register their applications to handle the search protocol and to be the default search application. Such applications need to support the search protocol syntax and register with the Default Programs feature to ensure a smooth and comfortable experience with Windows. “This LNK file points to a batch script (BAT) hosted on the same server, which, upon user click, could potentially trigger additional malicious operations,” Trustwave said, adding it could not retrieve the batch script due to the server being unresponsive. It’s worth noting that the abuse of search-ms: and search: as a malware distribution vector was documented by Trellix in July 2023.
BACKGROUND INTELLIGENT TRANSFER SERVICE (BITS):
Background Intelligent Transfer Service (BITS) is used by programmers and system administrators to download files from or upload files to HTTP web servers and SMB file shares. BITS will take the cost of the transfer into consideration, as well as the network usage so that the user’s foreground work has as little impact as possible. BITS also handles network interruptions, pausing and automatically resuming transfers, even after a reboot. BITS includes PowerShell cmdlets for creating and managing transfers as well as the BitsAdmin command-line utility.
Use BITS for applications that need to:
- Automatically resume file transfers after network disconnects and computer restarts.
- Preserve the responsiveness of other network applications.
- Be mindful of the network cost on e.g. roaming networks
REMEDIATION STEPS:
- Using unique and secure session cookies: It’s important to ensure that session identifiers are inaccessible to attackers once the session is closed. They should also be randomly generated and hard to crack by using brute force or other means.
- Limiting multipurpose cookies: Multipurpose cookies create a lot of security risks, so it is important to restrict each cookie for a single task.
- Using Hypertext Transfer Protocol Secure (HTTPS) communication: It is vital to use HTTPS communication to establish secure information flow and reduce the chances of attackers eavesdropping on cookie content.
- Having comprehensive session management:Ensuring strict and synchronous session management can increase cookie security and prevent poisoning attacks.
- Performing vulnerability scans: By regularly scanning web applications using a vulnerability scanner, security vulnerabilities that may lead to cookie poisoning can be proactively identified and eliminated.



