New Rust-based Fickle Malware Uses PowerShell for UAC Bypass and Data Exfiltration
A new Rust-based information stealer malware named Fickle Stealer has been identified, employing multiple attack chains to harvest sensitive information from compromised hosts. This blog delves into the intricacies of Fickle Stealer’s distribution methods, anti-analysis techniques, and data exfiltration mechanisms.
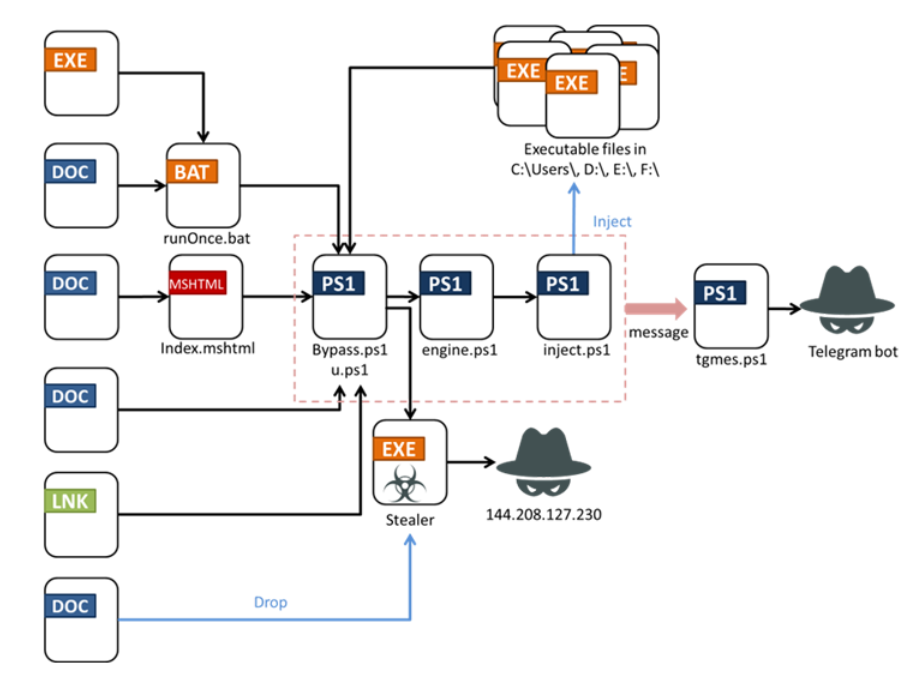
Distribution Methods
Fortinet FortiGuard Labs has observed four distinct distribution methods utilized by Fickle Stealer:
- VBA Dropper: This method leverages Visual Basic for Applications (VBA) scripts embedded in Office documents to deliver the malware.
- VBA Downloader: Similar to the VBA dropper, this technique involves VBA scripts that download the stealer from a remote server.
- Link Downloader: In this method, users are tricked into clicking on malicious links that directly download the malware.
- Executable Downloader: This method employs executable files that download and install the stealer on the victim’s machine.
PowerShell Script for UAC Bypass
Some of these methods incorporate a PowerShell script (bypass.ps1 or u.ps1) designed to bypass User Account Control (UAC). This script facilitates the execution of Fickle Stealer and periodically sends information about the victim, including:
- Country
- City
- IP Address
- Operating System Version
- Computer Name
- Username
The data is sent to a Telegram bot controlled by the attacker.
Anti-Analysis Techniques
The stealer payload is protected using a packer and runs a series of anti-analysis checks to evade detection. These checks include:
- Sandbox Detection: Verifies that the malware is not operating within a sandbox, a controlled environment typically used for analyzing malicious software.
- Virtual Machine Detection: Detects if the malware is being executed in a virtual machine.
Upon passing these checks, Fickle Stealer beacons out to a remote server to exfiltrate collected data in the form of JSON strings.
Targeted Applications and Data
Fickle Stealer is designed to gather information from various applications and file types:
Web Browsers
- Chromium-Based Browsers: Google Chrome, Microsoft Edge, Brave, Vivaldi
- Gecko-Based Browser: Mozilla Firefox
- Applications
- AnyDesk
- Discord
- FileZilla
- Signal
- Skype
- Steam
- Telegram
File Extensions
The malware searches for and exports files matching the following extensions:
- .txt
- .kdbx
- .doc, .docx
- .xls, .xlsx
- .ppt, .pptx
- .odt, .odp
- dat
In addition to these, Fickle Stealer searches for sensitive files in parent directories of common installation directories to ensure comprehensive data gathering. It also receives a target list from the server, enhancing its flexibility and targeting capabilities.
Comparison with AZStealer
The recent revelation of Fickle Stealer has followed closely after Symantec’s report on AZStealer, another information-stealing malware. AZStealer is a Python-based malware that is open-source and can be found on GitHub. It is being marketed as the “best undetected Discord stealer,” highlighting its primary focus on extracting sensitive information from Discord users while avoiding detection.
Features of AZStealer
Fickle Stealer employs sophisticated exfiltration methods to ensure the secure transfer of stolen information. Once the data is collected, it is compressed into zip files. These zipped files are then exfiltrated either directly through Discord webhooks, allowing the attacker to receive the data via Discord’s messaging platform, or initially uploaded to Gofile, an online file storage service. After uploading to Gofile, the files are subsequently exfiltrated through Discord, providing an additional layer of obfuscation and making the detection and tracking of the data theft more challenging.
The malware is meticulously designed to target a broad range of sensitive files. It attempts to steal documents with specific extensions, such as .txt, .pdf, .doc, .docx, .xls, .xlsx, .ppt, .pptx, .odt, .odp, and wallet.dat files. Moreover, Fickle Stealer scans for files that contain predefined keywords like “password,” “wallet,” “backup,” etc., in their filenames. This targeted approach ensures that the malware captures high-value information, enhancing the attacker’s ability to exploit the compromised data for financial gain or further malicious activities.
Remediation Steps:
- Implement Advanced Endpoint Protection: Deploy comprehensive endpoint security solutions that can detect and block malware like Fickle Stealer.
- Regular Software Updates: Ensure all systems and software are up to date with the latest security patches to prevent exploitation of vulnerabilities.
- Email and Web Filtering: Use email and web filtering solutions to block malicious attachments, links, and downloads that could deliver the stealer.
- User Education and Awareness: Conduct regular training sessions to educate employees about phishing attacks and the importance of not opening suspicious emails or attachments.
- Restrict PowerShell Usage: Limit the use of PowerShell scripts and implement strict execution policies to prevent unauthorized script execution.
- Network Segmentation: Segregate critical network segments to contain and minimize the impact of a potential breach.
- Regular Backups and Incident Response Plans: Maintain regular backups of critical data and have a robust incident response plan in place to quickly respond to and mitigate any security incidents.



