Military-themed Email Scam Spreads Malware to Infect Pakistani Users
Cybersecurity researchers have recently identified a new phishing campaign, named PHANTOM#SPIKE by Securonix, targeting individuals in Pakistan. This campaign employs military-related phishing documents to initiate an infection sequence using a custom backdoor. The threat actors distribute ZIP files containing password-protected payload archives through email, posing as meeting minutes from the International Military-Technical Forum Army 2024, a legitimate event organized by the Russian Ministry of Defense. Inside the ZIP archive, recipients find a Microsoft Compiled HTML Help (CHM) file and a hidden executable named “RuntimeIndexer.exe.” Opening the CHM file displays the meeting minutes and images, but stealthily executes the bundled binary upon user interaction. The executable functions as a backdoor, connecting to a remote server over TCP to retrieve and execute commands on the compromised host. This backdoor operates as a command line-based remote access trojan (RAT), allowing attackers to run commands, gather system information, and exfiltrate data back to the server. It uses commands like systeminfo, tasklist, curl to extract the public IP address via ip-api[.]com, and schtasks to establish persistence. The backdoor provides attackers with persistent, covert, and secure access to the infected system, enabling them to control the system, steal sensitive information, or deploy additional malware payloads. Despite its lack of sophistication, the PHANTOM#SPIKE campaign effectively uses simple payloads to achieve remote access, highlighting the need for robust email filtering, user education, endpoint protection, access controls, regular patching, network monitoring, and an incident response plan to mitigate such threats.
Attack Vector: ZIP Files with Password-Protected Payloads
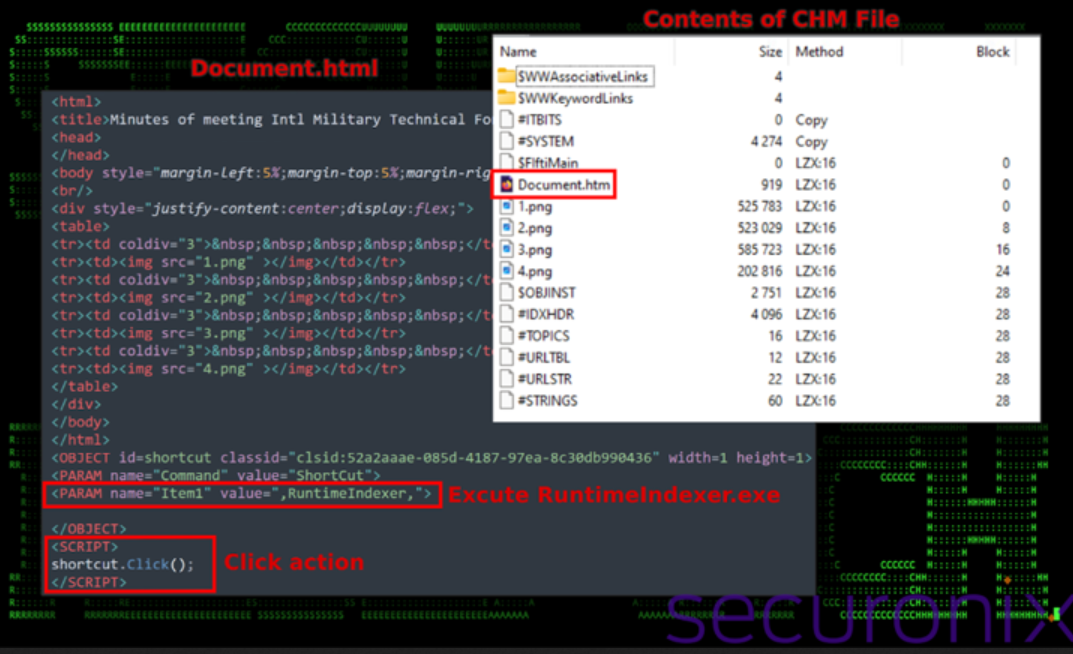
The threat actors behind PHANTOM#SPIKE utilize ZIP files with password-protected payload archives. Researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov explain that these ZIP files are distributed via email, posing as legitimate meeting minutes for the International Military-Technical Forum Army 2024. This event, organized by the Ministry of Defense of the Russian Federation, is slated to take place in Moscow in mid-August 2024. The malicious emails are crafted to appear credible, leveraging the authenticity of a well-known military event to entice recipients into opening the attached ZIP files. Once opened, the archive contains a Microsoft Compiled HTML Help (CHM) file and a hidden executable named “RuntimeIndexer.exe.” The CHM file displays the meeting minutes and images to the user, but stealthily executes the embedded binary when any part of the document is clicked. This execution activates a backdoor that connects to a remote server over TCP, allowing the attacker to retrieve and run commands on the infected host. The backdoor operates as a command line-based remote access trojan (RAT), executing commands like systeminfo for system details, tasklist for running processes, and curl to get the public IP address via ip-api[.]com. It also uses schtasks to establish persistence. This backdoor enables the attacker to maintain persistent, covert, and secure access to the compromised system, facilitating the theft of sensitive information or the deployment of additional malware payloads. The simplicity of the payloads, coupled with the sophisticated social engineering tactics, highlights the critical need for advanced email filtering, user training, robust endpoint protection, strict access controls, regular system updates, continuous network monitoring, and a comprehensive incident response plan to effectively counter such threats.
Infection Sequence: CHM File and Hidden Executable
Once operational, the backdoor collects the output of executed commands and exfiltrates this data back to the attacker’s server. Among the commands executed are systeminfo for system details, tasklist for running processes, and curl to extract the public IP address using ip-api[.]com. This capability grants the attacker persistent, covert, and secure access to the compromised system. With this access, they can steal sensitive information or deploy additional malware payloads. The backdoor’s command line-based remote access trojan (RAT) functionality allows it to execute commands remotely and relay the results back to the command and control (C2) server, giving the attacker control over the infected machine. It can set up persistence using schtasks, ensuring it remains active even after reboots. The attack demonstrates the effectiveness of relatively simple payloads in achieving significant control and data exfiltration. This underscores the critical need for robust cybersecurity measures such as advanced email filtering, comprehensive user education on recognizing phishing attempts, deployment and regular updating of endpoint protection software, strict access controls to prevent unauthorized application execution, consistent system and software patching, continuous network traffic monitoring for unusual activities, and a well-developed incident response plan to quickly address and mitigate breaches.
Functionality of the Backdoor
The executable “RuntimeIndexer.exe” serves as a backdoor, creating connections with a remote server over TCP. This backdoor is designed to retrieve and execute commands on the compromised host, effectively acting as a command line-based remote access trojan (RAT). Researchers have detailed several key capabilities of this backdoor. Firstly, it supports remote command execution, enabling the attacker to run commands on the infected system through cmd.exe, which allows for extensive manipulation of the system. Secondly, it possesses information-gathering capabilities, collecting various system details and exfiltrating this data back to the remote server, potentially including sensitive information about the system’s configuration and active processes. Thirdly, it incorporates a persistence mechanism, ensuring the backdoor remains active on the infected machine even after reboots. This is achieved through commands like schtasks, which schedule tasks that keep the backdoor operational. The backdoor’s functionality provides the attacker with persistent, covert, and secure access to the infected system, allowing them to control the system remotely, steal sensitive information, and potentially deploy additional malware payloads. This underscores the critical need for robust cybersecurity measures, including advanced email filtering, comprehensive user education, up-to-date endpoint protection software, strict access controls, regular system and software patching, continuous network traffic monitoring, and a well-prepared incident response plan to effectively counter such threats:
- Remote Command Execution: The backdoor allows the attacker to run commands on the infected system via cmd.exe.
- Information Gathering: It collects and exfiltrates system information back to the remote server.
- Persistence Mechanism: It uses commands like schtasks to set up persistence on the infected machine.
Data Exfiltration and Remote Control
Once operational, the backdoor collects the output of executed commands and exfiltrates this data back to the attacker’s server. Among the commands executed are systeminfo for system details, tasklist for running processes, and curl to extract the public IP address using ip-api[.]com. This capability grants the attacker persistent, covert, and secure access to the compromised system. With this access, they can steal sensitive information or deploy additional malware payloads. The backdoor’s command line-based remote access trojan (RAT) functionality allows it to execute commands remotely and relay the results back to the command and control (C2) server, giving the attacker control over the infected machine. It can set up persistence using schtasks, ensuring it remains active even after reboots. The attack demonstrates the effectiveness of relatively simple payloads in achieving significant control and data exfiltration. This underscores the critical need for robust cybersecurity measures such as advanced email filtering, comprehensive user education on recognizing phishing attempts, deployment and regular updating of endpoint protection software, strict access controls to prevent unauthorized application execution, consistent system and software patching, continuous network traffic monitoring for unusual activities, and a well-developed incident response plan to quickly address and mitigate breaches.
Remediation Steps for PHANTOM#SPIKE Campaign:
- Email Filtering: Implement advanced email filtering to detect and block phishing emails.
- User Education: Train employees to recognize phishing attempts and suspicious attachments.
- Endpoint Protection: Deploy and regularly update endpoint protection software to detect and prevent malware execution.
- Access Controls: Restrict user permissions to prevent the execution of unauthorized applications and scripts.
- Regular Patching: Ensure all systems and software are regularly updated with the latest security patches.
- Network Monitoring: Continuously monitor network traffic for unusual activity and potential exfiltration attempts.
- Incident Response Plan: Develop and maintain an incident response plan to quickly address and mitigate security breaches.



