Scattered Spider Web Tightens: Alleged Leader Arrested in Spain
In a major blow to a notorious cybercrime group, a key member of Scattered Spider was apprehended this week in Spain. Scattered Spider has been a thorn in the side of cybersecurity for the past two years, suspected of orchestrating a wave of attacks against high-profile companies like Twilio, LastPass, DoorDash, and Mailchimp. This arrest marks a significant development in the ongoing fight against cybercrime and could potentially disrupt the group’s operations.
Technical Details
Scattered Spider is known for employing a tactic called SIM swapping. This technique exploits vulnerabilities in mobile carrier systems or uses social engineering to gain control of a victim’s phone number. Here’s a deeper look at the technical aspects:
Social Engineering Techniques: Scattered Spider may target customer service representatives (CSRs) at mobile carrier companies. They might use tactics like:
- Vishing: Phishing calls where attackers impersonate legitimate representatives, attempting to trick CSRs into transferring phone numbers.
- Pretexting: Creating a fabricated scenario to manipulate CSRs into authorizing SIM swaps. This could involve claiming a lost or stolen phone or pretending to be an authorized representative of the victim.
- Exploiting Insider Threats: Scattered Spider may attempt to bribe or coerce insiders within mobile carrier companies to facilitate SIM swaps.
Technical Vulnerabilities: In some cases, Scattered Spider might exploit weaknesses in mobile carrier systems. This could involve:
- SS7 Flaws: The Signaling System 7 (SS7) is a set of protocols used for communication between telecommunications networks. Vulnerabilities in SS7 could allow attackers to intercept or redirect communication, potentially facilitating unauthorized SIM swaps.
- Weak Authentication: Mobile carriers might rely on outdated or easily guessable authentication methods for customer service representatives. Scattered Spider could exploit these weaknesses to gain unauthorized access to customer accounts and initiate SIM swaps.
- MFA Bypass Techniques: Once attackers gain control of the victim’s phone number, they can bypass multi-factor authentication (MFA) that relies on SMS verification codes. Here are some methods:
- SMS Interception: By controlling the phone number, attackers intercept any SMS verification codes sent by legitimate services.
- Port-out Attacks: Attackers might attempt to port the victim’s phone number to a different carrier controlled by them, allowing them to receive verification codes.
SIM swapping involves tricking a mobile carrier into transferring a victim’s phone number to a SIM card controlled by the attacker. This grants the attacker access to any verification codes sent via SMS, effectively bypassing multi-factor authentication (MFA) security measures that rely on text messages for authorization.
Scattered Spider’s attacks likely involved a combination of social engineering techniques to target victims and exploit weaknesses in mobile carrier security protocols. Social engineering could involve tactics like phishing emails or phone calls to trick victims into revealing personal information or clicking on malicious links.
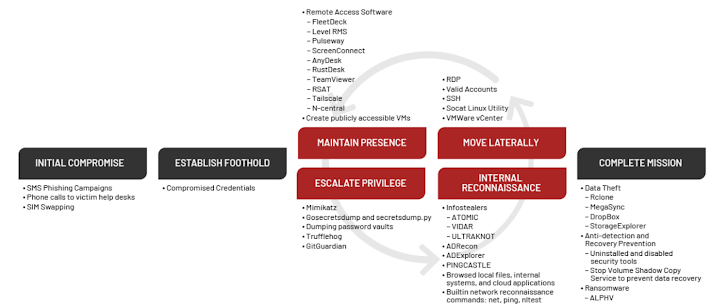
The arrested individual is a 22-year-old man from the United Kingdom, believed to be Tyler Buchanan from Dundee, Scotland. Spanish authorities apprehended him at Palma de Mallorca airport as he attempted to board a flight to Italy. Reports suggest this arrest is the result of a joint operation between the US Federal Bureau of Investigation (FBI) and the Spanish Police.
Buchanan, known online as “tylerb,” is suspected of being a central figure in Scattered Spider’s operations. This comes after the arrest of another alleged member, 19-year-old Noah Michael Urban of Florida, in January 2024. Urban, operating under the aliases “Sosa” and “King Bob,” is accused of stealing over $800,000 using similar methods.
The significance of Buchanan’s arrest lies in the potential disruption it could cause to Scattered Spider’s activities. Dismantling the leadership of a cybercrime group can significantly hinder its ability to launch coordinated attacks. Additionally, the international collaboration between the FBI and Spanish Police highlights a growing trend of law enforcement agencies working together to combat transnational cyber threats.
However, it’s important to note that cybercrime groups are often adaptable. Scattered Spiders may attempt to regroup or splinter into smaller fractions. Continued vigilance and international cooperation will be crucial to ensure this arrest is not a temporary setback but a turning point in the fight against this cybercrime group.
Remediation Steps
- Increase Awareness: Organizations and individuals should be made aware of SIM swapping scams and the importance of robust account security practices.
- MFA Implementation: Enforce multi-factor authentication (MFA) with security keys or biometrics as the preferred method over SMS verification.
- Regular Monitoring: Monitor accounts for suspicious activity and implement security protocols to detect and prevent unauthorized SIM swaps.
- Carrier Security: Mobile carriers should strengthen their verification procedures to make SIM swapping more difficult.
- Law Enforcement Cooperation: Continued collaboration between international law enforcement agencies is crucial to dismantle cybercrime organizations.
- Cybersecurity Hygiene: Practice good cyber hygiene such as using strong passwords, being cautious about clicking on links or opening attachments from unknown senders, and keeping software up to date.
- Incident Response Plan: Organizations should have an incident response plan in place to effectively address potential cyberattacks.



