Israeli Entities Targeted by Cyberattack Using Donut and Sliver Frameworks
In the constantly evolving landscape of cybersecurity, researchers have recently uncovered a sophisticated attack campaign targeting various Israeli entities using publicly available frameworks such as Donut and Sliver. This highly targeted campaign leverages target-specific infrastructure and custom WordPress websites as payload delivery mechanisms, affecting a diverse array of entities across unrelated verticals. According to a report by HarfangLab, a French cybersecurity firm, the attackers rely on well-known open-source malware to execute their operations. This blog will delve into the technical details, the nature of the attack, and the necessary remediation steps to mitigate such threats.
Technical Details of the Attack
The attack campaign employs a series of carefully orchestrated steps to infiltrate its targets.
- Vulnerability Type
The nature of the vulnerability lies in the misuse of publicly available malware frameworks like Donut and Sliver.
- Affected Products
The attack targets various Israeli entities, with a significant focus on exploiting custom WordPress websites. These sites are used as payload delivery mechanisms, making them a crucial component of the attack infrastructure.
- Impact
The impact of this cyberattack is substantial, with potential consequences including unauthorized access to sensitive data, data exfiltration, and possible espionage activities. The sophistication of the attack suggests that it could lead to significant disruptions in the affected entities.
Indicators of Compromise (IoCs)
Several IoCs have been identified in relation to this campaign:
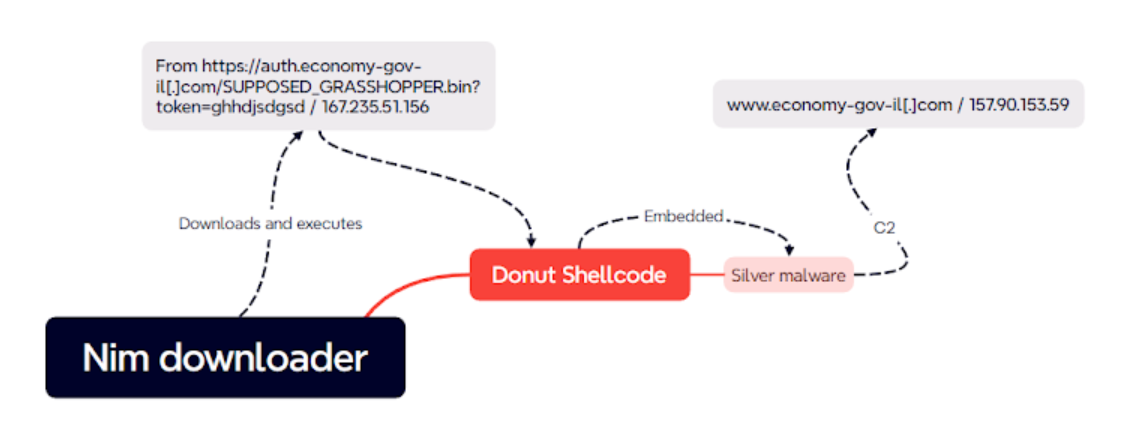
- Attacker-controlled server: economy-gov-il[.]com/SUPPOSED_GRASSHOPPER.bin
- Malicious file: Virtual Hard Disk (VHD) containing second-stage malware
- Frameworks involved: Donut and Sliver
Detection Rules
To detect and mitigate this threat, several detection rules can be implemented:
- Network Traffic Monitoring: Monitor for connections to suspicious domains, particularly auth.economy-gov-il[.]com.
- File Inspection: Inspect traffic for VHD file downloads from unfamiliar sources.
- Heuristic Analysis: Implement heuristic analysis to detect the use of Donut and Sliver frameworks.
The Attack’s Execution
The cyberattack on Israeli entities unfolds through a series of meticulously planned steps:
- Initial Compromise: The campaign begins with a first-stage downloader written in Nim. This downloader is designed to connect to an attacker-controlled server, specifically auth.economy-gov-il[.]com/SUPPOSED_GRASSHOPPER.bin.
- Payload Delivery: The first-stage downloader’s primary task is to download the second-stage malware from the staging server. This is achieved through a virtual hard disk (VHD) file, which is suspected to be disseminated via custom WordPress sites. This method is indicative of a drive-by download scheme, where unsuspecting users visiting these WordPress sites inadvertently download the malicious VHD file.
- Second-Stage Malware: The VHD file contains the Donut framework, a shellcode generation tool. Donut serves as a conduit for deploying Sliver, an open-source Cobalt Strike alternative. Sliver provides attackers with a robust platform for command and control operations, further enhancing their ability to infiltrate and manipulate target systems.
- Infrastructure and Deception: The attackers have put significant effort into acquiring dedicated infrastructure and deploying realistic-looking WordPress websites. This level of sophistication suggests a well-organized team, possibly operating with substantial resources. The use of legitimate-looking websites adds a layer of deception, making it harder for targets to recognize the threat.
Impact of the Attack
The implications of this cyberattack are far-reaching and severe:
- Unauthorized Access: The attackers can gain unauthorized access to sensitive information, potentially leading to data breaches and loss of intellectual property.
- Data Exfiltration: The use of sophisticated frameworks like Sliver allows for efficient data exfiltration, enabling attackers to steal valuable data undetected.
- Espionage: Given the targeted nature of the campaign, there is a strong possibility of espionage, with attackers potentially gathering intelligence on government or corporate activities.
- Operational Disruption: The attack can disrupt normal operations within affected entities, causing financial losses and damaging reputations.
Potential Legitimate Use
One intriguing aspect of this campaign is the possibility that it could be associated with legitimate penetration testing operations. HarfangLab theorizes that the sophisticated techniques and infrastructure used might indicate a sanctioned security testing exercise. If true, this raises important questions about the transparency of such operations and the ethical implications of impersonating Israeli government agencies.
Related Threats: Orcinius Trojan
In a related disclosure, the SonicWall Capture Labs threat research team detailed an infection chain involving booby-trapped Excel spreadsheets. These spreadsheets serve as the initial vector for delivering a trojan known as Orcinius. Here is a brief overview of this related threat:
- Initial Infection: The attack begins with Excel spreadsheets containing malicious VBA macros. When opened, these macros execute and initiate the download of the Orcinius trojan.
- Multi-Stage Payload Delivery: Orcinius is a multi-stage trojan that leverages cloud services like Dropbox and Google Docs to download additional payloads. This strategy helps the malware stay updated and maintain persistence on the infected system.
- Persistence Mechanisms: Orcinius employs several techniques to ensure it remains active on the target system. It hooks into Windows to monitor running processes and keystrokes, and it creates persistence through registry key modifications.
Remediation Steps
Given the complexity and potential impact of this attack campaign, it is crucial to implement robust remediation strategies. Here are several steps that can help mitigate the risk:
- Network Segmentation: Implementing network segmentation is a critical step in limiting the spread of malware. By dividing the network into smaller, isolated segments, it becomes more challenging for attackers to move laterally across systems.
- Update and Patch Management: Regularly updating and patching all software, including operating systems, applications, and frameworks, is essential. This helps close vulnerabilities that attackers might exploit.
- Implement Multi-Factor Authentication (MFA): Enforcing multi-factor authentication (MFA) adds an extra layer of security, making it harder for attackers to gain unauthorized access even if they obtain valid credentials.
- Employee Training: Conducting regular cybersecurity awareness training for employees is crucial. Training should focus on recognizing phishing attempts, suspicious activities, and safe browsing practices.
- Monitor and Analyze Network Traffic: Using advanced monitoring tools to detect abnormal network behavior can help identify potential threats early. This includes monitoring for unusual connections, large data transfers, and access to critical resources.
- Regular Backups: Performing regular backups of critical data ensures that, in the event of an attack, data can be restored without significant loss. It is essential to store backups securely and test them periodically for restoration.
- Use Security Solutions: Deploy comprehensive security solutions such as antivirus, anti-malware, and intrusion detection/prevention systems. These tools provide multiple layers of defense against various types of cyber threats.
- Incident Response Plan: Developing and maintaining an incident response plan is vital for quickly addressing and mitigating cybersecurity incidents. The plan should outline the steps to take in the event of an attack, including communication protocols, containment strategies, and recovery procedures.



