ExCobalt Cyber Gang Targets Russian Sectors with New GoRed Backdoor
Russian organizations have been targeted by a cybercrime gang known as ExCobalt, utilizing a previously unknown Golang-based backdoor called GoRed. Positive Technologies researchers, Vladislav Lunin and Alexander Badayev, disclosed this information in a technical report published this week. ExCobalt, believed to be composed of former members of the notorious Cobalt Gang, has been active since at least 2016 and focuses on cyber espionage. Cobalt Gang was infamous for attacking financial institutions to steal funds, using tools like CobInt, which ExCobalt adopted in 2022. Over the past year, ExCobalt has targeted various sectors in Russia, including government, information technology, metallurgy, mining, software development, and telecommunications, showcasing a high degree of sophistication in their attacks.
ExCobalt’s method of initial access to target environments involves leveraging previously compromised contractors and executing supply chain attacks. The attackers infect a component used in building the target company’s legitimate software. This sophisticated approach reflects ExCobalt’s advanced capabilities.
Once inside the network, ExCobalt employs a variety of tools to execute commands on infected hosts. These tools include:
- Metasploit: A penetration testing framework used for developing and executing exploit code.
- Mimikatz: A tool to extract plaintext passwords, hashes, PIN codes, and Kerberos tickets from memory.
- ProcDump: A command-line utility used to monitor an application for CPU spikes and generate crash dumps during a spike.
- SMBExec: A post-exploitation tool that enables command execution on remote hosts via SMB.
- Spark RAT: A remote access tool for executing commands on infected hosts.
The attackers also exploit several Linux privilege escalation vulnerabilities such as:
- CVE-2019-13272
- CVE-2021-3156
- CVE-2021-4034
- CVE-2022-2586
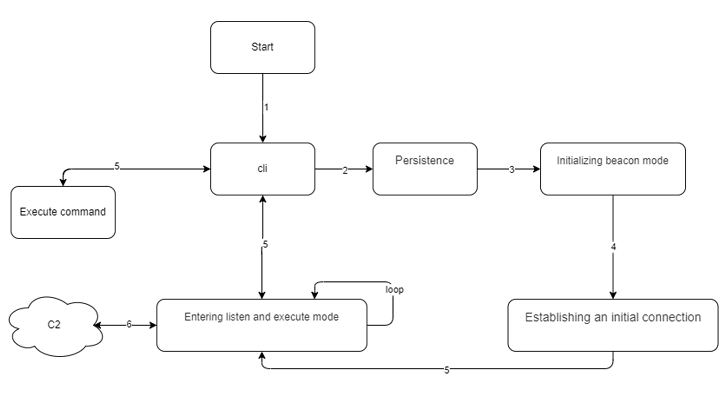
GoRed, the custom backdoor used by ExCobalt, has undergone numerous iterations and is a comprehensive tool that allows operators to:
- Execute commands
- Obtain credentials
- Harvest details of active processes, network interfaces, and file systems
GoRed communicates with its command-and-control (C2) server using the Remote Procedure Call (RPC) protocol. It supports various background commands to monitor files of interest, capture passwords, and enable reverse shells. The collected data is then exported to attacker-controlled infrastructure.
ExCobalt’s recent activities have demonstrated their high level of sophistication and adaptability in targeting Russian companies across multiple sectors. The group’s flexibility and versatility are evident in their toolset, which includes both custom tools like GoRed and modified standard utilities that help bypass security controls and adapt to evolving protection methods.
The researchers from Positive Technologies highlighted ExCobalt’s continuous development and enhancement of their techniques, showcasing their determination and persistent threat to targeted entities. This cybercrime gang’s adoption of tools like CobInt and their innovative use of supply chain attacks mark a significant evolution from their origins in the Cobalt Gang.
The technical report underscores the high degree of threat posed by ExCobalt, as their attacks are not only well-coordinated but also exhibit a keen understanding of their targets’ environments. The utilization of previously compromised contractors and sophisticated supply chain attacks suggests that ExCobalt is likely to continue their aggressive campaigns with increasing effectiveness.
Remediation steps:
- Patch Management: Ensure all systems are promptly updated with the latest security patches. This includes patching the specific vulnerabilities (CVE-2019-13272, CVE-2021-3156, CVE-2021-4034, and CVE-2022-2586) mentioned in the report, along with any newly discovered vulnerabilities.
- Multi-Factor Authentication (MFA): Implement MFA wherever possible. This adds an extra layer of security beyond passwords and makes it significantly harder for attackers to gain access even if they steal credentials.
- Endpoint Detection and Response (EDR): Deploy EDR solutions to continuously monitor your network for suspicious activity. EDR systems can detect malware, malicious behavior, and potential intrusions, allowing for a swift response.
- Supply Chain Security Review: Conduct a thorough review of your supply chain security practices. This includes evaluating the security posture of third-party vendors and the components used in your organization’s software. Look for potential vulnerabilities that attackers might exploit.
- Security Awareness Training: Provide regular security awareness training to employees. Train them to identify phishing attempts, social engineering tactics, and other techniques that ExCobalt might use to gain initial access. This can significantly reduce the risk of successful attacks.
- Network Segmentation: Implement network segmentation to isolate critical systems and data from less sensitive areas of your network. This can limit the damage caused by a potential breach and make it harder for attackers to move laterally within your network.
- Incident Response Plan: Develop and test a comprehensive incident response plan. This plan should outline the steps to take in case of a security breach, including containment, eradication, recovery, and reporting.



