Windows Update Vulnerabilities Exposed: CVE-2024-38202 and CVE-2024-21302
Recent discoveries by SafeBreach Labs, led by researcher Alon Leviev, have exposed critical security vulnerabilities within the Windows operating system. These vulnerabilities, which were highlighted during presentations at Black Hat USA 2024 and DEF CON 32, present a significant threat by potentially allowing downgrade attacks on the Windows update architecture. Such attacks could enable malicious actors to replace current, secure OS files with outdated and vulnerable versions, effectively undermining the system’s security. The vulnerabilities, designated as CVE-2024-38202 and CVE-2024-21302, have prompted Microsoft to begin developing security updates to mitigate these risks and protect users from the associated threats.
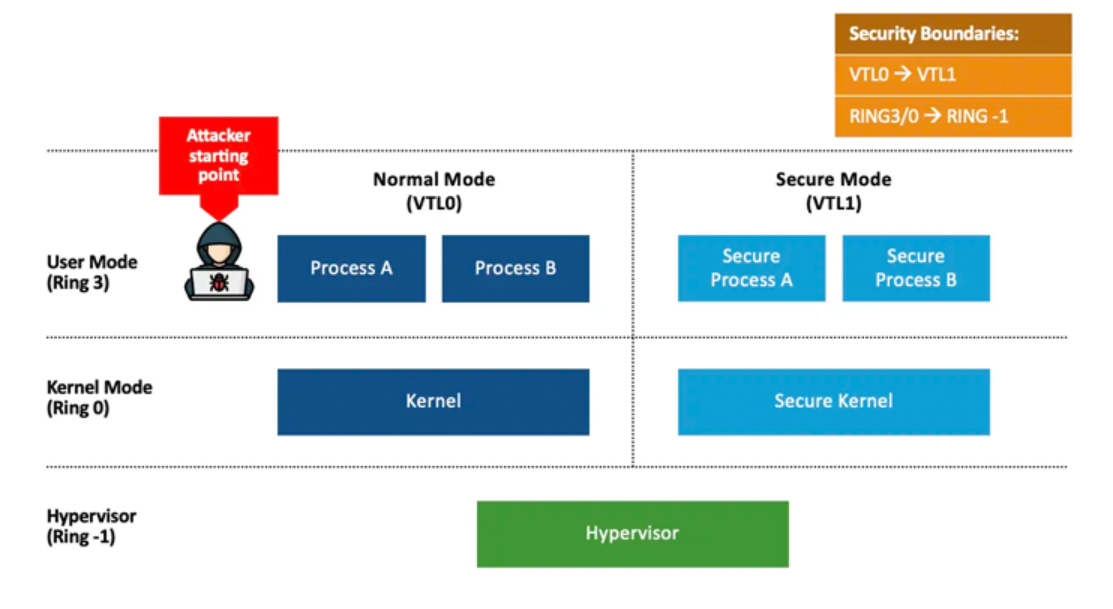
CVE-2024-38202: Windows Update Stack Elevation of Privilege Vulnerability
CVSS Score: 7.3
Description:
CVE-2024-38202 originates from the Windows Backup component and concerns elevation of privilege vulnerabilities within the Windows update mechanism. This flaw allows an attacker with basic user privileges to reintroduce previously mitigated vulnerabilities or bypass features of Virtualization Based Security (VBS).
Exploitation Scenario:
To exploit this vulnerability, an attacker would need to convince an Administrator or a user with delegated permissions to perform a system restore, inadvertently triggering the vulnerability. The flaw could enable the attacker to restore outdated or compromised system components, potentially undermining the integrity of the operating system.
Impact:
- Reintroduction of previously addressed vulnerabilities
- Circumvention of Virtualization Based Security (VBS) features
CVE-2024-21302: Windows Secure Kernel Mode Elevation of Privilege Vulnerability
CVSS Score: 6.7
Description:
CVE-2024-21302 is a privilege escalation vulnerability affecting Windows systems that support VBS. This flaw allows an adversary to replace current versions of Windows system files with older, potentially insecure versions.
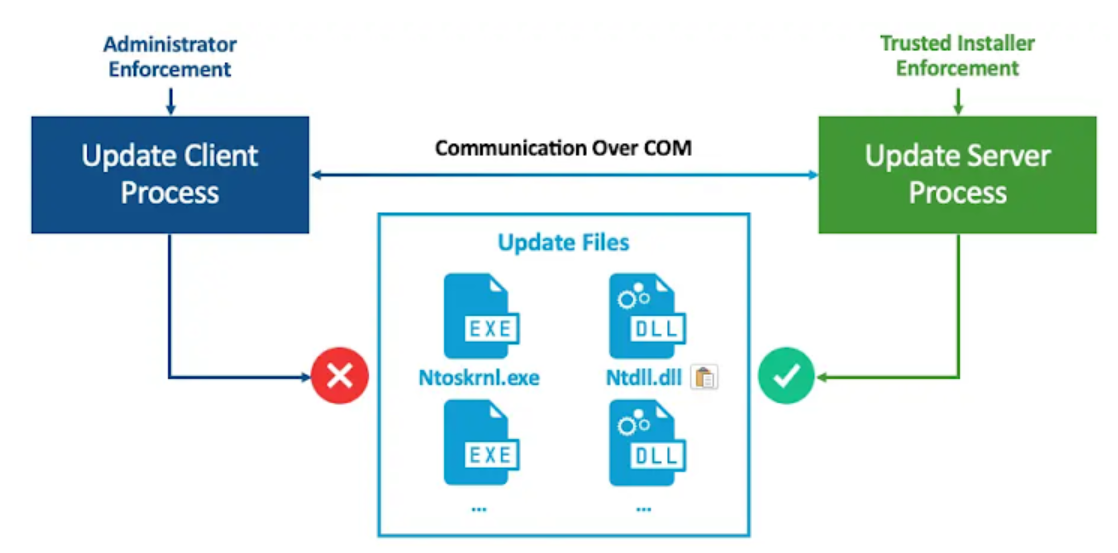
Exploitation Scenario:
An attacker exploiting this vulnerability could use a tool such as Windows Downdate to perform persistent and invisible downgrades of critical OS components. This tool can bypass verification steps including integrity verification and Trusted Installer enforcement, allowing downgrades of dynamic link libraries (DLLs), drivers, and the NT kernel.
Impact:
- Reintroduction of fixed vulnerabilities as new zero-days
- Bypass of security features including VBS, Credential Guard, and Hyper-V’s hypervisor
- Potential exposure of sensitive data protected by VBS
- Prevention of future updates and hindrance of detection by recovery tools
The Windows Downdate Tool
Leviev’s presentation detailed the Windows Downdate tool, which can exploit these vulnerabilities to perform “irreversible downgrades” on critical OS components. This tool manipulates the Windows Update process to craft undetectable and persistent downgrades, allowing attackers to elevate privileges and bypass security features.
Capabilities of Windows Downdate:
- Bypasses verification steps like integrity checks and Trusted Installer enforcement
- Downgrades critical system components, including DLLs, drivers, and NT kernel
- Exposes previously patched vulnerabilities as active threats
- Disables features such as Hypervisor-Protected Code Integrity (HVCI) and Credential Guard’s Isolated User Mode Process
Significance:
The ability to bypass the security features of Windows VBS and Hyper-V highlights a critical design flaw. This flaw has persisted since the introduction of VBS in 2015, indicating a long-standing vulnerability in the virtualization stack that could impact the security posture of Windows systems globally.
Remediation Steps for CVE-2024-38202 and CVE-2024-21302
To mitigate the risks posed by the vulnerabilities CVE-2024-38202 and CVE-2024-21302, follow these remediation steps:
- Apply Security Updates: Immediately apply Microsoft’s security patches when released.
- Restrict System Restore Privileges: Limit system restore capabilities to trusted administrators only.
- Strengthen Virtualization Based Security (VBS): Ensure VBS, Secure Boot, and HVCI are enabled and correctly configured.
- Implement Multi-Factor Authentication (MFA): Require MFA for all administrative and privileged accounts.
- Monitor for Downgrade Attacks: Use EDR tools and monitor update logs for signs of downgrade attacks.
- Implement Least Privilege Principle: Limit user privileges to the minimum necessary for their roles.
- Regular Backup and Recovery Planning: Regularly back up critical data and test recovery procedures.
- Awareness and Training: Educate users on phishing risks and provide ongoing security training.
- Deploy a Patch Management Solution: Automate patch deployment and regularly audit patch status.
- Engage with Security Vendors: Consult experts and leverage threat intelligence for proactive defense.



