Industrial Remote Access Tool Ewon Cosy+ Vulnerable to Root Access Attacks
The Ewon Cosy+ industrial remote access solution has been discovered to contain critical security vulnerabilities that could allow attackers to gain unauthorized root access to devices. These flaws pose serious risks to industrial infrastructure, enabling potential attackers to decrypt sensitive data, hijack VPN sessions, and carry out additional malicious activities. The vulnerabilities include an operating system command injection and a persistent cross-site scripting (XSS) issue, both of which can be exploited to escalate privileges and take control of devices. Moreover, the system’s reliance on device serial numbers for certificate generation can be manipulated, allowing threat actors to hijack VPN sessions by enrolling their own certificates, effectively overwriting the original device’s session. This enables attackers to intercept and redirect network communication, potentially leading to further attacks on connected systems. These vulnerabilities were uncovered by SySS GmbH security researcher Moritz Abrell and presented at DEF CON 32, highlighting the urgent need for remediation to protect industrial environments relying on Ewon Cosy+.
Overview of Ewon Cosy+ Architecture
Ewon Cosy+ is built to enable secure remote access to industrial gateways using a VPN connection, with its architecture centered around a vendor-managed platform called Talk2m and utilizing OpenVPN for VPN relays. This configuration allows technicians to remotely connect to industrial systems, ensuring secure communication. However, this setup also introduces potential security risks, as it opens several attack vectors that could be exploited by malicious actors. While the system is designed for secure remote access, the reliance on external management and VPN technology inherently carries vulnerabilities that must be carefully managed to prevent unauthorized access and ensure the integrity of connected industrial infrastructure.
Vulnerabilities Discovered
- Operating System Command Injection and Filter Bypass
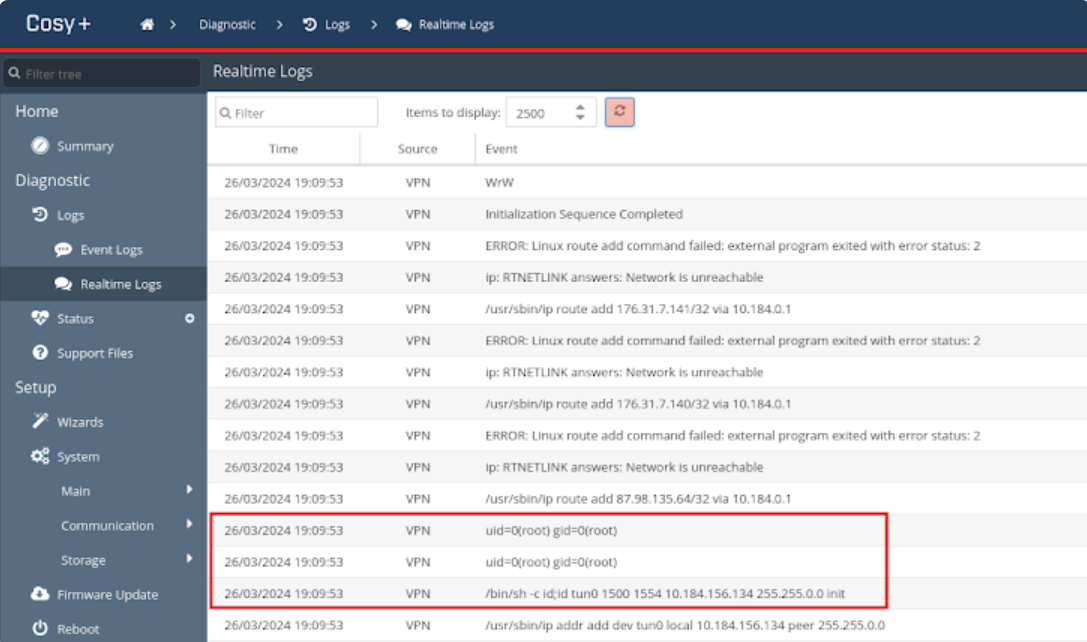
SySS GmbH discovered a critical operating system command injection vulnerability within Ewon Cosy+. By uploading a specially crafted OpenVPN configuration file, attackers could bypass existing security filters and execute arbitrary commands on the system. This vulnerability enables attackers to obtain a reverse shell, providing them with unauthorized access to the underlying operating system.
- Persistent Cross-Site Scripting (XSS) and Credential Exposure
Another significant vulnerability identified was a persistent cross-site scripting (XSS) flaw. This issue, combined with the fact that the device stores Base64-encoded credentials in an unprotected cookie named “credentials,” allows an attacker to gain administrative access. Once administrative access is achieved, the attacker can escalate privileges to root, compromising the entire system.
- VPN Session Hijacking via Serial Number Exploitation
The communication between the Cosy+ and the Talk2m API is secured via HTTPS and mutual TLS (mTLS) authentication. However, the security of this communication is undermined by a flaw in the certificate generation process. Specifically, the device’s serial number is used as the common name (CN) in the certificate signing request (CSR). An attacker who knows or guesses a target device’s serial number could exploit this to enroll their own CSR, hijack the VPN session, and overwrite the original device’s session. This would allow the attacker to redirect users connecting via the Ecatcher VPN client software to their own malicious system.
Attack Chain and Potential Impact
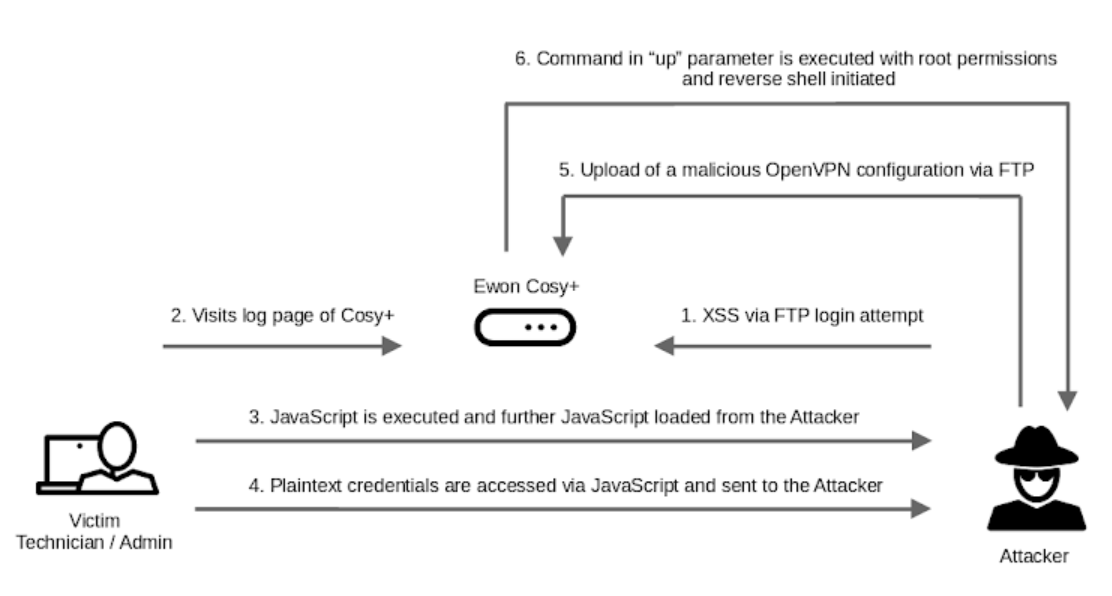
- Gaining Root Access
An unauthenticated attacker could combine the identified vulnerabilities to gain root access to the Cosy+. For example, by waiting for an administrative user to log in, the attacker could exploit the XSS vulnerability and the exposed credentials to escalate privileges.
- Establishing Persistence and Decrypting Sensitive Data
With root access, the attacker could set up persistence on the device, allowing them to maintain control even after reboots or security updates. Additionally, they could access firmware-specific encryption keys, decrypt firmware update files, and extract sensitive information using a hard-coded key found in the binary for password encryption.
- Further Exploitation of VPN Session Hijacking
Once the VPN session is hijacked, the attacker could conduct a range of further attacks. For instance, they could access network services such as RDP or SMB on the victim’s client machine. The unrestricted nature of the tunnel connection further facilitates these attacks, enabling the attacker to imitate the original network and systems to intercept user input, including uploaded PLC programs.
Broader Implications: OpenVPN Vulnerabilities
The vulnerabilities identified in Ewon Cosy+ are especially troubling when considered alongside recent discoveries by Microsoft, which revealed multiple flaws within OpenVPN itself. These OpenVPN vulnerabilities can be exploited in combination to achieve remote code execution (RCE) and local privilege escalation (LPE), significantly amplifying the risks posed by the flaws in Ewon Cosy+. The potential for these vulnerabilities to be chained together highlights a broader threat, making it even more critical to address the security issues in both Ewon Cosy+ and the underlying OpenVPN framework to protect against potential attacks.
Remediation Steps
- Apply Patches: Update Ewon Cosy+ devices with the latest firmware patches released by the vendor to address identified vulnerabilities.
- Enhance Input Validation: Implement stricter input validation on configuration files to prevent command injection attacks.
- Secure Cookies: Encrypt session cookies and store them securely to prevent unauthorized access to credentials.
- Implement Multi-Factor Authentication (MFA): Enforce MFA for administrative access to reduce the risk of unauthorized login attempts.
- Monitor VPN Sessions: Regularly monitor VPN sessions for unusual activity and enforce session timeouts.
- Restrict Network Access: Limit network access to essential services only and apply strict firewall rules to minimize attack surfaces.
- Conduct Regular Security Audits: Perform periodic security audits and penetration testing to identify and address new vulnerabilities.



