GitHub Vulnerability ‘ArtiPACKED’ Exposes Repositories to Potential Takeover
The discovery of a security vulnerability in GitHub Actions artifacts, named ArtiPACKED, has raised significant concerns in the developer and cybersecurity communities. Uncovered by researchers at Palo Alto Networks’ Unit 42, this attack vector allows malicious actors to potentially take over repositories and gain unauthorized access to cloud environments. The vulnerability arises from a combination of misconfigurations and security flaws in GitHub Actions artifacts, which can lead to the leakage of sensitive tokens, including GitHub tokens and third-party cloud service tokens. These tokens, once exposed, could be exploited to compromise services and gain unauthorized access. Particularly concerning is the exposure of an undocumented environment variable, ACTIONS_RUNTIME_TOKEN, which could be used to substitute an artifact with a malicious version, opening the door for remote code execution when developers download and execute the rogue artifact. The vulnerability has been observed in open-source repositories related to major tech companies such as AWS, Google, Microsoft, Red Hat, and Ubuntu. GitHub has categorized the issue as informational, urging users to secure their uploaded artifacts. Organizations must take proactive steps to mitigate this risk by restricting artifact access, monitoring for unauthorized access, enforcing least privilege, updating workflows, encrypting sensitive data, and regularly rotating tokens. This vulnerability underscores the importance of securing CI/CD workflows to protect repositories and cloud environments from emerging threats.
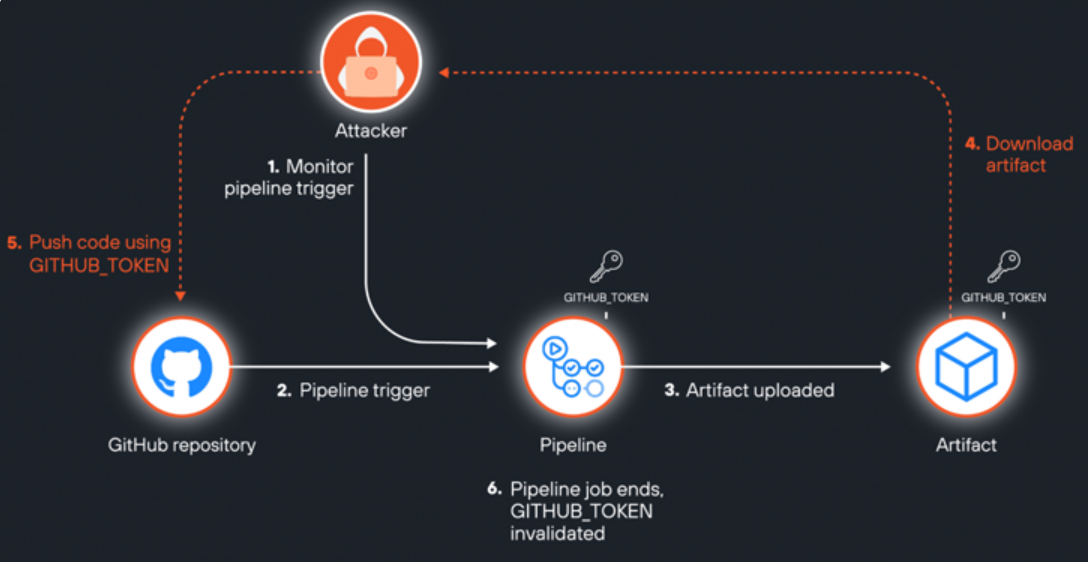
The Anatomy of ArtiPACKED
Misconfigurations and Security Flaws
The ArtiPACKED vulnerability stems from a mix of misconfigurations and security flaws in GitHub Actions artifacts. These artifacts, which play a crucial role in sharing data between jobs and storing information for up to 90 days after a workflow is completed, can unintentionally expose sensitive information. This exposure makes them a prime target for attackers. The vulnerability highlights the risks associated with improperly secured artifacts, which can lead to the leakage of critical data and unauthorized access.
Leakage of Sensitive Tokens
Researchers have discovered that GitHub Actions artifacts can leak sensitive tokens, such as GitHub tokens (GITHUB_TOKEN and ACTIONS_RUNTIME_TOKEN), as well as tokens for third-party cloud services. These tokens are crucial for accessing repositories and other related services. If exposed, they become highly valuable to attackers, who can exploit them to gain unauthorized access and potentially compromise critical services. This vulnerability underscores the importance of securing tokens within artifacts to prevent them from becoming a gateway for malicious activities.
Public Availability of Artifacts
In open-source projects, artifacts are publicly accessible to anyone with read access to the repository. This public availability becomes a severe security concern when it leads to the exposure of sensitive tokens. The most concerning revelation is the exposure of an undocumented environment variable called ACTIONS_RUNTIME_TOKEN. This token, with a lifespan of approximately six hours, can be exploited to substitute an artifact with a malicious version before it expires.
Exploiting the Vulnerability
Remote Code Execution
The exposure of ACTIONS_RUNTIME_TOKEN opens a dangerous attack window. If a developer downloads and executes a rogue artifact, or if a subsequent workflow job is configured to run based on previously uploaded artifacts, remote code execution (RCE) becomes a very real possibility.
Token Expiry and Race Conditions
While GITHUB_TOKEN typically expires when a job ends, the ArtiPACKED vulnerability introduces a new dimension of risk. With the improvements made to the artifacts feature in version 4, attackers could exploit race conditions to steal and use the token by downloading an artifact while a workflow run is still in progress. This stolen token could then be used to push malicious code to the repository by creating a new branch before the pipeline job ends and the token is invalidated. However, this attack relies on the workflow having the contents: write permission.
Real-World Implications
Susceptibility of Major Repositories
The ArtiPACKED attack has been observed in open-source repositories related to major tech giants, including Amazon Web Services (AWS), Google, Microsoft, Red Hat, and Ubuntu. The exposure of these repositories to such an attack underscores the gravity of the vulnerability and the widespread risk it presents to both open-source and proprietary projects.
GitHub’s Response
GitHub has categorized this issue as informational, placing the responsibility on users to secure their uploaded artifacts. While this response might seem insufficient, it highlights the importance of organizations taking proactive steps to secure their workflows and protect sensitive information.
Mitigation Strategies
Reevaluating Artifact Usage
Organizations must reevaluate the way they use GitHub Actions artifacts, especially in light of GitHub’s deprecation of Artifacts V3. Overlooked elements like build artifacts often become prime targets for attackers, and it’s crucial to implement stringent security measures to safeguard these resources.
Implementing Best Practices
Some best practices to mitigate the risk include:
- Restricting Access: Limit who can access and download artifacts, especially in public repositories.
- Monitoring Artifacts: Regularly monitor and audit artifacts for any signs of unauthorized access or tampering.
- Securing Tokens: Use the least privileged access for tokens, and ensure that tokens are only available for the necessary duration.
- Updating Workflows: Review and update workflows to remove unnecessary permissions, such as contents: write, that could be exploited in an attack.
Remediation Steps:
- Restrict Artifact Access: Limit who can access and download artifacts, particularly in public repositories.
- Monitor and Audit Artifacts: Regularly review artifacts for unauthorized access or tampering.
- Enforce Least Privilege: Configure tokens with minimal permissions and restrict their lifespan.
- Update Workflows: Remove unnecessary permissions, such as contents: write, from workflows.
- Implement Artifact Encryption: Encrypt sensitive data in artifacts to prevent unauthorized access.
- Use Secure Storage: Store artifacts in secure, access-controlled environments rather than in publicly accessible locations.
- Regularly Rotate Tokens: Frequently rotate GitHub tokens to minimize the impact of potential leaks.



