GiveWP WordPress Plugin Vulnerability Puts 100,000+ Websites at Risk
WordPress, a leading content management system, remains a frequent target for cyberattacks, particularly through its extensive plugin ecosystem. Recently disclosed severe vulnerabilities in several widely-used WordPress plugins have exposed thousands of websites to significant risks. If these vulnerabilities are not promptly addressed, they could enable attackers to execute remote code, read and delete sensitive files, escalate user privileges, and compromise critical data. These security flaws underscore the importance of maintaining up-to-date plugins and implementing robust security measures to protect WordPress sites from potential breaches and unauthorized access.
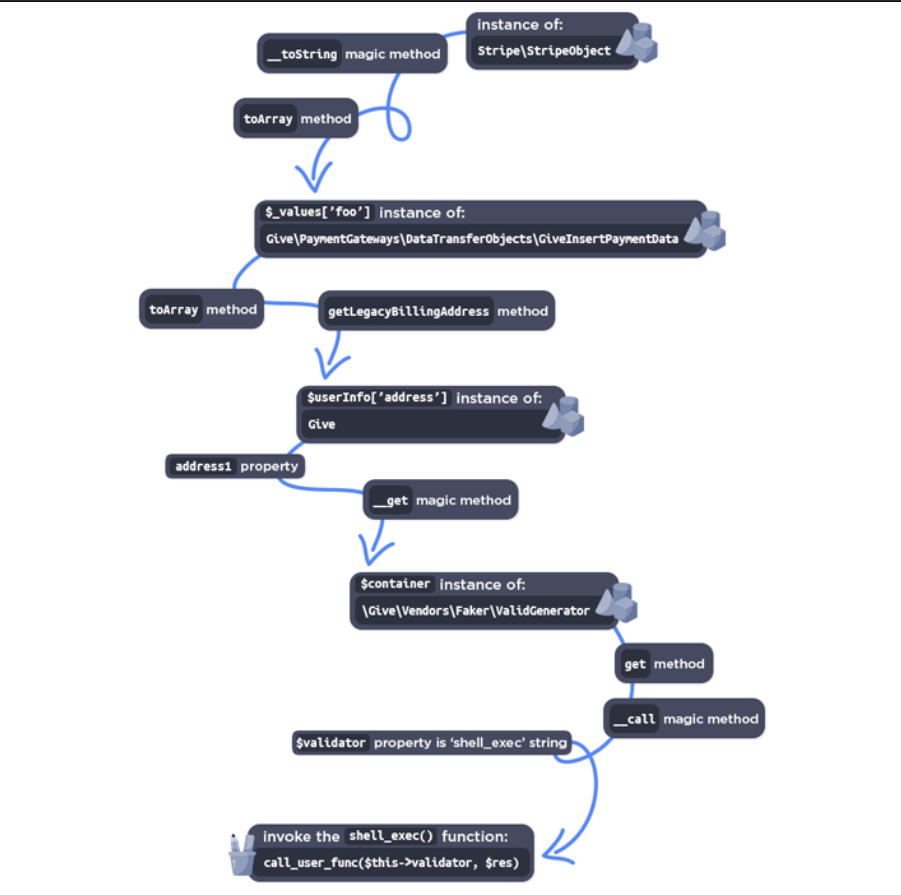
CVE-2024-5932: GiveWP Donation Plugin Vulnerability
Vulnerability Type: PHP Object Injection
CVSS Score: 10.0
Affected Versions: All versions prior to 3.14.2
Discovered by: villu164
A critical flaw has been identified in the GiveWP Donation and Fundraising plugin, a tool used by over 100,000 websites. This vulnerability, rooted in the give_process_donation_form() function, allows unauthenticated attackers to inject a PHP object via the give_title parameter. The presence of a POP (Property-Oriented Programming) chain further enables remote code execution and arbitrary file deletion. Website administrators are strongly urged to update to version 3.14.2 immediately.
CVE-2024-6500: InPost PL and InPost for WooCommerce Plugin Vulnerability
Vulnerability Type: Arbitrary File Read and Delete
CVSS Score: 10.0
Affected Versions: All versions prior to 1.4.5
This vulnerability affects the InPost PL and InPost for WooCommerce plugins, allowing unauthenticated attackers to read and delete arbitrary files, including the critical wp-config.php file. On Linux systems, while file deletion is limited to the WordPress directory, all files can still be read, posing a significant risk. Version 1.4.5 has been released to address this issue.
CVE-2024-7094: JS Help Desk Plugin Vulnerability
Vulnerability Type: PHP Code Injection
CVSS Score: 9.8
Affected Versions: All versions prior to 2.8.7
The JS Help Desk plugin, with over 5,000 active installations, is vulnerable to a PHP code injection flaw. This vulnerability allows remote code execution, potentially giving attackers full control over the affected site. Users should update to version 2.8.7 as soon as possible.
Other Critical Vulnerabilities in WordPress Plugins
Several other WordPress plugins have also been found to contain high-severity vulnerabilities:
CVE-2024-6220: Keydatas Plugin
Vulnerability Type: Arbitrary File Upload
CVSS Score: 9.8
Impact: Allows unauthenticated attackers to upload arbitrary files, leading to potential code execution.
CVE-2024-6467: BookingPress Appointment Booking Plugin
Vulnerability Type: Arbitrary File Read
CVSS Score: 8.8
Impact: Allows authenticated attackers to read sensitive files and execute arbitrary code.
CVE-2024-5441: Modern Events Calendar Plugin
Vulnerability Type: Arbitrary File Upload
CVSS Score: 8.8
Impact: Allows authenticated attackers to upload and execute malicious files.
CVE-2024-6411: ProfileGrid Plugin
Vulnerability Type: Privilege Escalation
CVSS Score: 8.8
Impact: Allows authenticated users to escalate their privileges to an Administrator level.
WordPress plugins
The recently disclosed vulnerabilities in popular WordPress plugins pose a serious threat to the security of thousands of websites that depend on them. Exploiting these flaws could allow unauthenticated attackers to execute remote code, access and delete sensitive files, and even escalate their privileges to the administrator level. The most critical issue, CVE-2024-5932 in the GiveWP donation plugin, could enable attackers to deploy malicious code, such as credit card skimmers, compromising sensitive financial information from site visitors. Similarly, vulnerabilities in the InPost PL, InPost for WooCommerce, and JS Help Desk plugins also allow for remote code execution, potentially giving attackers full control of affected websites. Other flaws, while less severe, still pose significant risks, such as unauthorized access to sensitive data or privilege escalation, as seen in the ProfileGrid plugin (CVE-2024-6411). These incidents underscore the necessity of maintaining a strong security posture by keeping WordPress installations and plugins up-to-date, as failure to do so can expose websites to a broad spectrum of attacks, including skimming, defacement, and data breaches.
Indicators of Compromise (IoCs)
To detect potential exploitation, administrators should monitor for:
- Unauthorized file uploads or modifications.
- Suspicious PHP objects or payloads in request parameters.
- Unusual activity from low-privilege user accounts.
- Anomalous changes to user capabilities or roles.
Detection Rules:
- Monitor attempts to access vulnerable plugin functions like give_process_donation_form() and others associated with the vulnerabilities.
- Detect unusual file modifications or creations within the WordPress installation directory.
- Analyze user activity and privilege changes for potential privilege escalation attempts.
Remediation Steps:
- Update Plugins: Immediately update the affected plugins to their latest versions.
- Security Monitoring: Implement robust security monitoring to detect and respond to potential attacks.
- Backup Regularly: Ensure regular backups of WordPress site data and configuration files for quick recovery.
- Restrict Permissions: Limit user permissions and access levels to the minimum required.
- Use a WAF: Consider implementing a Web Application Firewall (WAF) or a Content Delivery Network (CDN) for added protection.
- User Education: Educate users on security best practices, including the use of strong passwords and avoiding untrusted plugins.
- Traffic Monitoring: Monitor website traffic for any suspicious patterns that could indicate an ongoing attack.