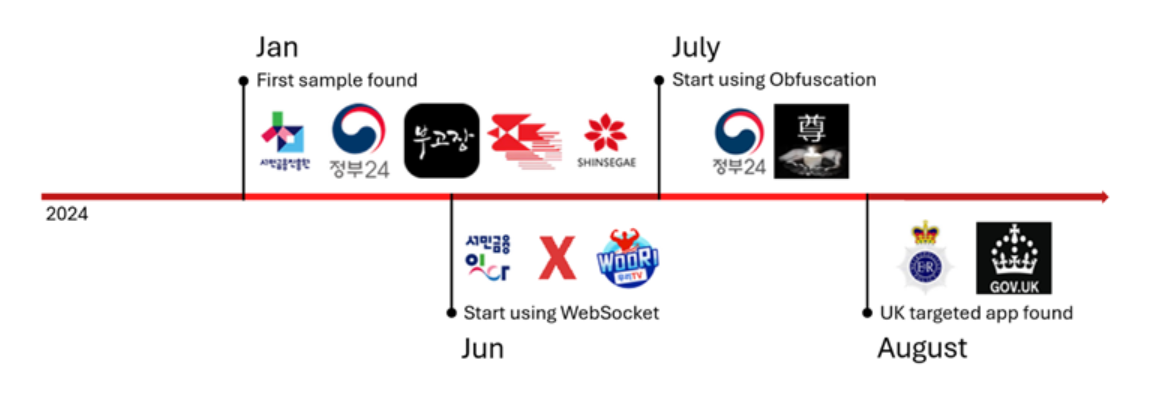
New Mobile Malware Campaign Targeting Android Users in South Korea and Beyond
A new mobile malware campaign has emerged, initially targeting Android users in South Korea and now spreading to the U.K., introducing a novel threat called “SpyAgent.” This malware is particularly dangerous for cryptocurrency wallet users, as it employs advanced techniques to steal mnemonic keys by scanning images on compromised devices. Disguised as legitimate banking, government, streaming, and utility apps, SpyAgent infiltrates devices through SMS messages with malicious links, leading users to download APK files from deceptive websites. Once installed, the malware requests extensive permissions to access sensitive data, including contacts, SMS messages, and photos, which are then exfiltrated to an external server controlled by the attackers. Notably, SpyAgent leverages Optical Character Recognition (OCR) technology to identify and steal mnemonic keys, a critical security measure for cryptocurrency wallets. The campaign’s command-and-control infrastructure has significant security flaws, exposing victim data and enabling remote control of infected devices. Recently, SpyAgent shifted from using simple HTTP requests to WebSocket connections for communication with its C2 server, enhancing its ability to evade detection by traditional security tools. This development underscores the evolving sophistication of mobile malware threats and the heightened risk to users globally.
Malware Overview: SpyAgent
Targeting and Infection Methodology
SpyAgent primarily targets Android users through fake applications disguised as legitimate banking, government, streaming, and utility apps. These bogus apps are distributed via SMS messages containing malicious links, leading users to download APK files from deceptive websites. Once installed, these apps request intrusive permissions to gain access to sensitive data on the device.
Intrusive Permissions and Data Exfiltration
After installation, SpyAgent gains access to a wide range of data, including contacts, SMS messages, photos, and other critical device information. This data is then exfiltrated to an external server controlled by the threat actors. The most notable feature of SpyAgent is its ability to use Optical Character Recognition (OCR) technology to steal mnemonic keys—critical recovery or seed phrases that allow users to regain access to their cryptocurrency wallets.
Command-and-Control Infrastructure

Security Lapses and Data Exposure
McAfee Labs’ analysis revealed significant security lapses within the malware’s command-and-control (C2) infrastructure. These lapses allowed researchers to navigate the C2 server’s root directory without authentication, exposing gathered data from victims. Furthermore, the C2 server hosts an administrator panel that enables remote control of infected devices, raising concerns about broader targeting, including iOS devices.
Transition to WebSocket Communications
SpyAgent initially relied on basic HTTP requests for communication with its command-and-control (C2) server. However, the malware has recently transitioned to using WebSocket connections, representing a major tactical shift. This change enhances SpyAgent’s ability to engage in more efficient, real-time, two-way communication with its C2 server, enabling the malware to respond more dynamically to commands and making it harder for security measures to detect. The adoption of WebSocket connections also allows SpyAgent to bypass traditional network monitoring tools that typically focus on HTTP traffic, increasing its stealth and effectiveness as a cyber threat. This upgrade reflects the growing sophistication of modern malware, as it adapts to evade detection and maintain persistent control over infected devices.
Broader Context: CraxsRAT and Related Threats
Comparison to CraxsRAT
The rise of SpyAgent closely follows the CraxsRAT campaign, an Android Remote Access Trojan (RAT) active since at least February 2024. CraxsRAT primarily targeted banking users in Malaysia and Singapore, distributing its payload through phishing websites. Similar to SpyAgent, CraxsRAT possesses advanced spyware capabilities, enabling remote control of infected devices. This includes keylogging, screen recording, and unauthorized access to sensitive data, highlighting the growing sophistication of mobile threats. Both malware strains represent significant risks, particularly to financial institutions and users, as they exploit vulnerabilities to gain control over devices and compromise critical information
Remediation Steps:
- Avoid Suspicious Links: Never click on links from unknown SMS messages or emails.
- Install Apps from Trusted Sources: Only download apps from official app stores like Google Play.
- Regular Security Updates: Keep your device’s operating system and apps updated to patch vulnerabilities.
- Use Mobile Security Software: Install and maintain reputable mobile security software to detect and block malware.
- Limit App Permissions: Only grant necessary permissions to apps, and review them regularly.
- Backup Data: Regularly backup your data to secure locations to mitigate potential loss from attacks.



