New “Raptor Train” IoT Botnet Compromises Over 200,000 Devices Worldwide
Security researchers have recently uncovered a large-scale botnet targeting small office/home office (SOHO) and Internet of Things (IoT) devices, attributed to a Chinese state-sponsored threat actor, commonly referred to as Flax Typhoon (also known as Ethereal Panda or RedJuliett). The botnet, named Raptor Train by Lumen’s Black Lotus Labs, has been in operation since at least May 2020 and is believed to have compromised a peak of 60,000 devices in June 2023.
The Scale of Raptor Train Botnet
As of June 2023, over 200,000 devices including SOHO routers, network video recorders (NVRs), digital video recorders (DVRs), network-attached storage (NAS) servers, and IP cameras have been conscripted into the Raptor Train botnet. This makes it one of the largest state-sponsored IoT botnets ever identified.
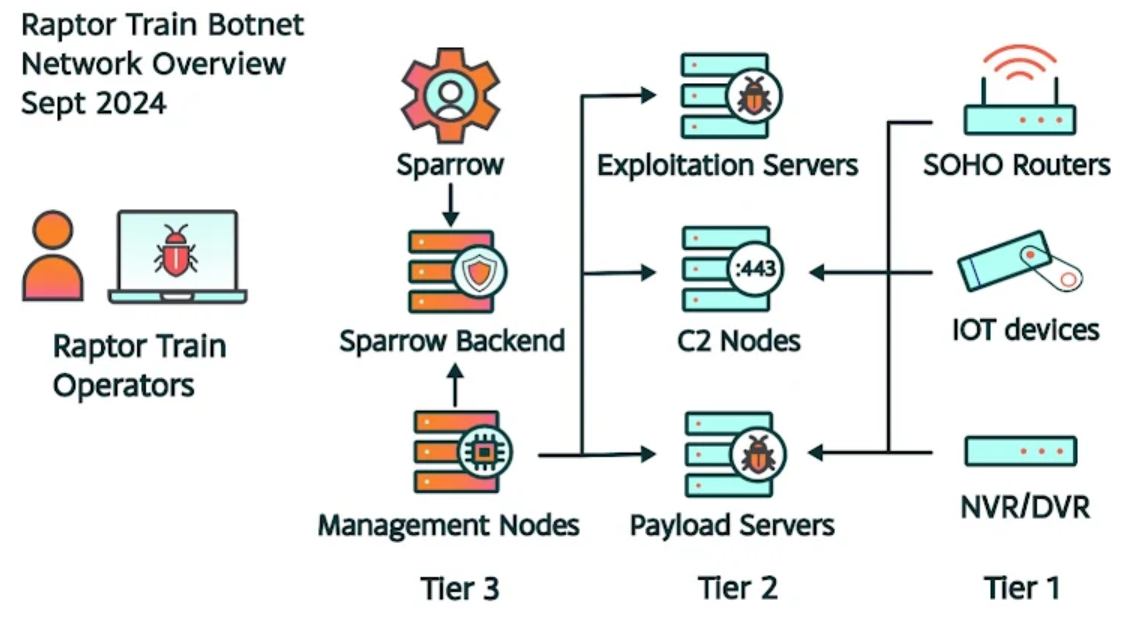
The botnet’s infrastructure utilizes a three-tiered architecture, which is a sophisticated design allowing centralized control and flexible exploitation:
- Tier 1: Compromised SOHO/IoT devices
- Tier 2: Exploitation servers, payload servers, and command-and-control (C2) servers
- Tier 3: Centralized management nodes powered by a cross-platform Electron application named Sparrow, also known as the Node Comprehensive Control Tool (NCCT).
Attack Lifecycle: Exploitation and Command Execution
The management nodes in Tier 3 initiate bot tasks that flow through Tier 2 C2 servers before being passed down to Tier 1 devices. The targeted devices include routers, IP cameras, DVRs, and NAS units from manufacturers like ActionTec, ASUS, DrayTek, Hikvision, QNAP, Synology, and many others.
A majority of the Tier 1 devices are geolocated in the U.S., Taiwan, Vietnam, Brazil, Hong Kong, and Turkey. These devices have an average lifespan of 17.44 days, highlighting the re-exploitability of vulnerable devices due to the botnet operators’ reliance on a vast array of available exploits.
Notably, the threat actors behind Raptor Train did not implement a persistent mechanism that survives a device reboot. However, the sheer number of vulnerable devices connected to the internet allows for reinfection at will, giving the botnet what Lumen has referred to as “inherent persistence.”
Infection and Exploitation Tools: Mirai Variant Nosedive
The infection method involves an in-memory implant known as Nosedive, a custom variant of the well-known Mirai botnet. Nosedive is distributed via Tier 2 payload servers and is capable of executing various commands, uploading and downloading files, and launching DDoS attacks.
Tier 2 nodes, which serve as C2 servers and exploitation servers, rotate every 75 days, with most of these servers located in the U.S., Singapore, the U.K., Japan, and South Korea. Since 2020, the number of active C2 nodes has increased significantly, growing from just a few in 2020 to 60 nodes by mid-2024.
Campaigns: Evolution of the Raptor Train Botnet
Since mid-2020, the botnet has evolved through multiple campaigns, each characterized by distinct domains and targeted devices. The campaigns are as follows:
- Crossbill (May 2020 – April 2022): Utilized the root domain k3121.com
- Finch (July 2022 – June 2023): Operated under the domain b2047.com
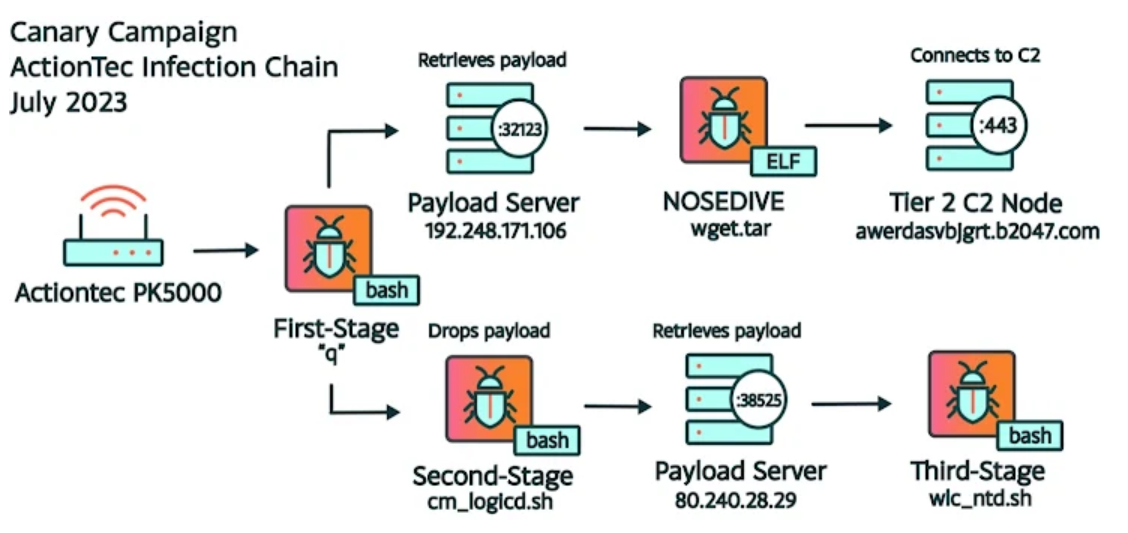
- Canary (May 2023 – August 2023): Employed multi-stage droppers and targeted devices like Hikvision IP cameras and ASUS routers
- Oriole (June 2023 – September 2024): Featured the root domain w8510.com and included multi-layered infection chains.
During the Canary campaign, the botnet focused on ActionTec modems, Hikvision IP cameras, and ASUS routers. The infection process involved a series of bash scripts downloaded from Tier 2 servers. Each layer of the infection script was designed to periodically download and execute subsequent payloads.
Domain Prominence and Circumventing Security
One concerning aspect of the Oriole campaign is the prominence of the w8510.com domain in IoT devices, which made its way into Cisco Umbrella and Cloudflare Radar’s top 1 million domains by mid-2024. Domains that appear on these whitelists often evade security measures, further allowing the botnet to grow unchecked and avoid detection.
Targets and Impact
Although the Raptor Train botnet has not been directly linked to any DDoS attacks, evidence suggests that it has been used to target U.S. and Taiwanese entities in critical sectors such as military, government, telecommunications, and IT. The botnet has also likely attempted exploitation of Atlassian Confluence servers and Ivanti Connect Secure (ICS) appliances in these sectors.
The botnet’s links to Flax Typhoon, a Chinese threat actor group, are evident in the overlap of targeted regions and sectors, as well as the use of similar tactics and language.
FBI Dismantles Raptor Train Botnet
In a coordinated law enforcement effort, the U.S. Department of Justice (DoJ) dismantled the Raptor Train botnet. The DoJ attributed the botnet’s operation to a publicly-traded Chinese company known as Integrity Technology Group. Through a court-authorized operation, the FBI was able to seize control of the infrastructure, issuing commands to the infected devices and disabling the malware.
The botnet had grown to over 260,000 compromised devices by June 2024, with devices located across North America, Europe, Asia, and beyond. The operation revealed over 1.2 million records of compromised devices stored in a MySQL database hosted on the Tier 3 management server, which was controlled via the Sparrow application.
Remediation Steps:
- Patch Vulnerabilities: Ensure all SOHO/IoT devices are updated with the latest firmware and security patches.
- Disable Unnecessary Services: Turn off unused services on devices to reduce attack surface.
- Implement Strong Authentication: Enforce strong, unique passwords and enable multi-factor authentication (MFA) on all devices.
- Segregate Networks: Isolate IoT devices on separate networks from critical systems.
- Monitor for Anomalous Activity: Continuously monitor device traffic for unusual patterns or unauthorized access.
- Block Malicious Domains: Blacklist domains associated with botnet C2 servers (e.g., com).
- Factory Reset Infected Devices: Perform a factory reset on compromised devices to remove malware.
- Harden Device Configuration: Disable default credentials and restrict remote management features on all IoT devices.



