
What is a Honeypot As Service?
Today, many attackers are a part of organized crimes with the intent to defraud their victims. Their goal is to deploy malware on a victim’s machine and to start collecting sensitive data, such as online account credentials and credit card numbers. Since attackers have a tendency to take the path of least resistance and many traditional attack paths are barred by a basic set of security measures, such as firewalls or anti-virus engines, the “black hats” are turning to easier, unprotected attack paths to place their malware onto the end user’s machine. That is why we need to allocate shadow monitoring to the servers so that we can stay one step ahead of them.
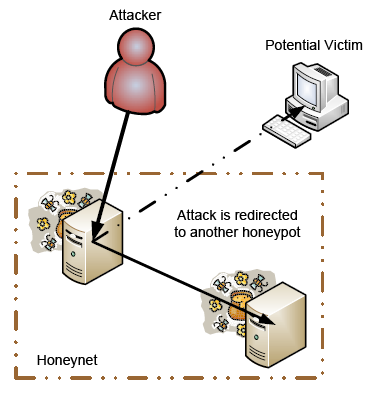
Apart from shadow surveillance we also need to redirect any potential attack to the contained sandbox so that any attack cannot leak sensitive data while without making any external actor suspicious. So that we will have the total security surveillance with an active protection system.

Applicability
As in current scenario, the cyber-attacks orchestrated on any organization have been done in a silent manner. A honeypot system configuration can drastically improve any company security standard.
We here at CyberSRC® deliver our honeypot service in two different modes for better applicability
Monitoring Mode:
Here we are using our traffic module for one-way transmission of the traffic for further analysis of the traffic.
Redirection Mode:
Here we are using our clone module with filtering module for establishing a security suite for achieving both surveillance with active mitigation of attacks.
Benefits:
- Monitor & Detect The Attackers And Their Method Of Attacking:
As the attacker will be using multiple attack methods, the traffic will be analysed by different systems configured to dissect the traffic in various scopes - Improve Organization’s Security Posture:
A honey-net system increases security posture of any organization tenfold as traffic data is now analysed in real-time and can be also used in incident management cases - Prevent Damage To The Company Reputation:
Any high level attack against the server, will be detected and alerted by the SIEM. Organization can mitigate any impending cyber-attack in real-time.
Objective
Here the objective of the project is to provide a complete security solution for any organization.
By providing full range of security measures in their IT infrastructure namely Monitoring of the data and Web application firewall.
Our aspiration here is to build a stealth system which will mitigate and analyse the any cyber-attack done to the organization infrastructure subtlety without being detected.
Approach
Traditional honeypot systems work only as surveillance systems whether they are low interaction system or high interaction system. As they are either situated outside the internal network or they are supplied with the duplicate data of the server.
In our CyberSRC® honeypot solution we have created a honeypot system where our core objective is to provide an Active Security Protection to the server.
Here our motive is to protect the production server actively while establishing a honey-net system for analysis of any attacks done on the system.
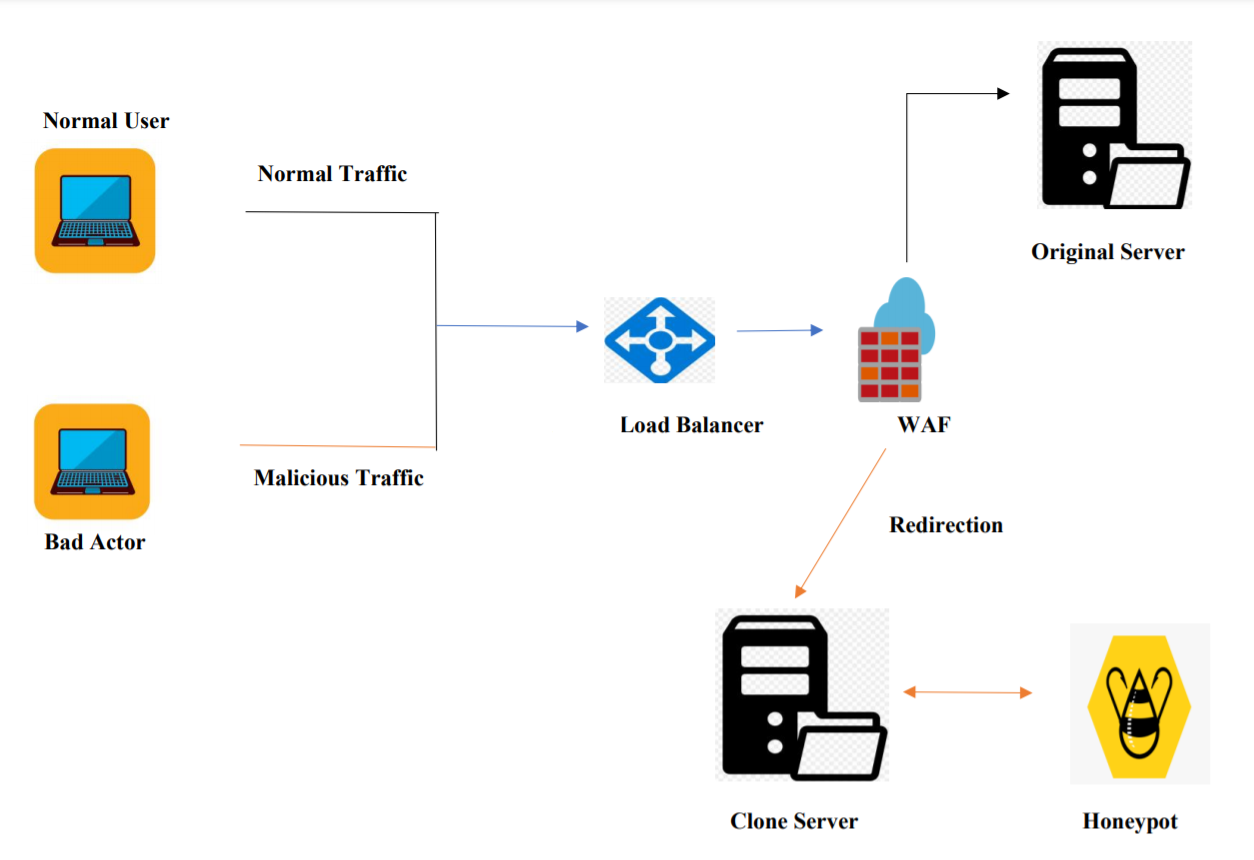
As shown in the above figure all the external actors will interact with the application gateway where their request will be inspected for routing of the packets based on the rules set to deflect any possible malicious action.
Furthermore any network based attack will be also mitigated by the system and recorded in the system for further analysis
Methodology
Web Application Protection:
Any request targeted for the client web application will pass through the Web Application Firewall (WAF) which will inspect the packet data to either allow it to the application or deny it according to the configuration.
Network Application Protection:
Similar to the web application, every request targeted to the client server will pass through network filter where the request can be allowed to the server or it will be dropped according to the filter configuration.
Shadow Surveillance:
Our intention here is to hide the presence of the honeypot systems from any external actor (good or bad) so that we can analyse the traffic for any attack and build security measures against it
Why CyberSRC®?
Established in January 2018, CyberSRC® Consultancy offers the full machination of cyber security services ranging from threat intelligence, VMS to general advisory services in areas pertaining to Cyber security such as vulnerability attacks, compliance, and cyber security regulations, and laws. We are into system audits such as ISNP Audits, NBFC Audits, UCB Audits, PPI Audits, and SEBI Audits. We provide our solutions with better accountability. We are a certified assurance firm. We are an ISO 27001 certified organization, backed by a very diverse and dynamic team which have a combined experience.
