FLUBOT MALWARE
An international law enforcement investigation involving 11 countries, including Australia, Belgium, Finland, Hungary, Ireland, Romania, Spain, Sweden, Switzerland, the Netherlands, and the United States, has brought down one of the fastest-spreading mobile malware named FluBot. FluBot, also known as Cabassous is an Android malware that steals passwords, online bank details, and other sensitive data from infected cell phones all around the world. It was called flu due to its rapid and extensive spread. It spreads mostly through smishing (also known as SMS-based phishing) messages, which trap users into clicking on a link to download malware-laced software. It can also retrieve SMS data, make phone calls, and observe incoming notifications for temporary authentication codes such as one-time passwords (OTP), which are required in standard login credentials. While it was originally an android malware, it has recently been developed to target iOS users with users being routed to phishing sites and subscription scams when they attempt to view the infected links.
WORKING OF FLUBOT MALWARE
FluBot can spread in a variety of ways. Text messages are the most common vectors. The malware sends out messages in German, Polish, and Hungarian to its victims. The user is directed to click on a link in the text message to track their out-for-delivery parcel. Other variations of the message direct consumers to a phishing link where they may check their voicemail or download a critical security update. The user is redirected to a webpage after clicking the link. The homepage either asks the visitor to download a tracking software for delivery services like FedEx and DHL, a voicemail app or a security update, depending on the contents of the message. Surprisingly, the fake security update informs customers that they have been attacked with FluBot and that the upgrade would assist in its removal.
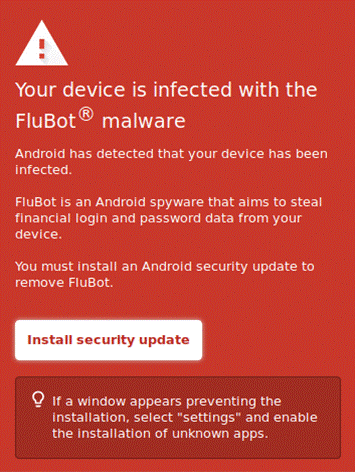
If the user agrees, FluBot-infected APK files are downloaded and installed on their device. The application asks for permission to access contact lists, read and write text messages, and make phone calls throughout the installation process. In other words, the app gets control of the most crucial functionalities on the device. FluBot is identical to a trojan virus as it disguises itself as a helpful application to infect a computer.
REMOVAL OF FLUBOT MALWARE
The FluBot malware can be removed by any of the following methods –
- The malware should be removed by restoring the device to factory defaults if the device has already been infected by it. If a user wishes to recover from a backup, then it must be ensured that the backup is free of malware. It is a good idea to change the passwords on any accounts that were accessed through the compromised device.
- The user can try to delete the infected app using Android Safe Mode by long-pressing the Power button and selecting “Reboot in Safe Mode,” which will allow the user to enter Safe Mode though this varies between devices.
- If a user feels the device was infected while using a banking application then the bank should be informed and their recommendations should be followed. The user should continuously monitor all the transactions and quickly report any fraudulent activity.
- If an iPhone user has unintentionally subscribed to premium services via a FluBot SMS, then the carrier should be contacted to cancel the subscription and, if possible, a permanent block should be applied to future subscriptions to the services.
After the user has uninstalled FluBot from the system then the local cyber-crime unit should be informed that the device of the user has been compromised. This will allow the cyber-crime unit to keep an eye on the malware and protect other users.
PREVENTION FROM FLUBOT MALWARE
The users can avoid getting infected with FluBot malware by doing the following:
- Installation of an antivirus scanner can be done on Android devices as it will aid in the identification and removal of not only FluBot but also other malware such as worms and keyloggers.
- Two-factor authentication can be used on all accounts, particularly for banks and other financial organizations. FluBot may be unable to reach the second level of authentication even if it has our password.
- To download apps a user should only use reliable sources. Before downloading an app, some research should be done on the software and its creators. If accessible other people’s reviews and ratings should be seen. Users should be careful of links in emails and text messages that may trap them into installing software from unknown or third-party sources.
- Links or attachments in inappropriate emails or text messages should not be clicked and should be deleted right away.
- Shortened URLs and QR codes should be double-checked because they may drive to malicious websites or download malware directly to devices.
- It is recommended to log out of websites after making a payment, rather than just shutting the browser, once the transaction is completed.
- Usernames and passwords should never be saved in mobile browsers or apps.
- Public wi-fi should not be used for banking or online shopping.
- Operating systems and apps should be kept up to date by downloading software updates for the operating system of the device when prompted.



