Critical RCE Bug Could Allow Hackers to Monitor and Control DrayTek Vigor Routers
In 29 various DrayTek router models, a new serious remote code execution vulnerability has been discovered that, if exploited, might result in the complete compromise of the target device and unauthorized network access.
Philippe Laulheret, a Trellix researcher, claims that if the device’s management interface has been set up to be internet facing, the attack can be executed without any user intervention. “A one-click assault can also be executed from within the LAN in the normal device configuration.”
The vulnerability, listed under CVE-2022-32548, has been awarded the highest severity rating of 10.0 on the CVSS scoring system due to its ability to completely enable an attacker to take control of the routers.
The main issue is a buffer overflow inside the web management interface (“/cgi-bin/wlogin.cgi”), which a malicious actor might exploit by submitting well-constructed information. By entering properly constructed username and/or password strings that are base64 encoded into the fields aa and ab of the login page, an attacker can exploit the vulnerability. The absence of size verification for these encoded strings is the main cause of the issue.
The result of this attack is the so-called “DrayOS,” which implements router functionality, being taken over, according to Laulheret. It is therefore possible to switch to the underlying operating system and establish a dependable footing on the device and local network on devices that have an underlying Linux operating system (such as the Vigor 3910).
Hackers that take advantage of this weakness might do the following things:
- Complete device takeover,
- Data access,
- Setting up covert man-in-the-middle assaults,
- Changing DNS settings,
- Utilizing routers as DDoS or crypto miner bots, or
- Switching to devices linked to the compromised network are all possibilities.
Widespread Effect
DrayTek Vigor devices capitalized on the “work from home” trend to become extremely well-known during the epidemic. For VPN connectivity to small- and medium-sized business networks, they are outstanding, cost-effective products.
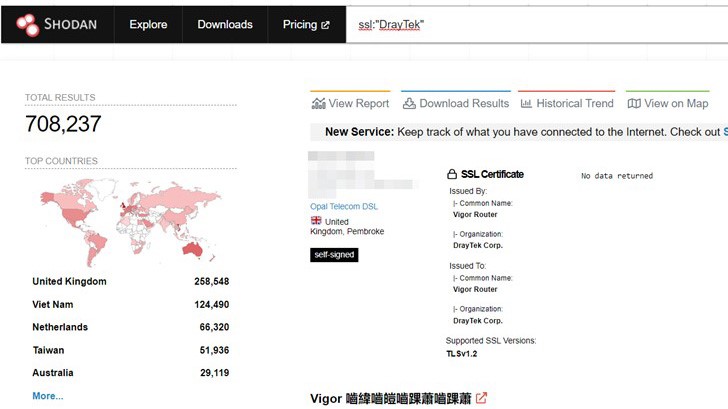
Over 700,000 online devices were found in a Shodan search, with the majority being in the UK, Vietnam, Netherlands, and Australia.
Due to its popularity, Trellix decided to assess the security of one of DrayTek’s flagship models and discovered that the web management interface has a buffer overflow problem on the login page.
One can exploit the weakness and take over the OS of the device by entering a specially created pair of credentials as base64 encoded strings in the login fields.
According to reports, the insecure service is present on over 200,000 devices made by the Taiwanese company and may be accessed without any user involvement. Many of the remaining 500,000 devices are vulnerable to one-click attacks even when they are not exposed to the outside world.
Trellix commends the manufacturer for their excellent responsiveness and the prompt distribution of a fix less than 30 days after the issue of the vulnerability was disclosed to their security team. The vendor has already provided a patch to address the vulnerability in DrayTek devices.
According to the researchers, the hacking of a network appliance like the Vigor 3910 can result in the following consequences:
- leakage of private information on the router (keys, administrative passwords, etc.)
- Access to the internal LAN resources that would often require a VPN connection or be part of the “same network”
- A person standing in the way of network traffic
- monitoring DNS queries and other unencrypted traffic sent from the LAN through the router to the internet
- capturing packets of data travelling across any router port
- Botnet usage (DDoS, hosting malicious data, etc.)
- leakage of private information on the router (keys, administrative passwords, etc.)
- leakage of private information on the router (keys, administrative passwords, etc.)
- leakage of private information on the router (keys, administrative passwords, etc.)
Attempts at exploitation that fail can result in:
- Restarting the gadget
- Disruption of Service on the impacted devices
- Additional potential improper conduct
Our general best practice guideline is to always keep firmware up to date, but we recommend that you verify to make sure affected systems are running at least the firmware version.



