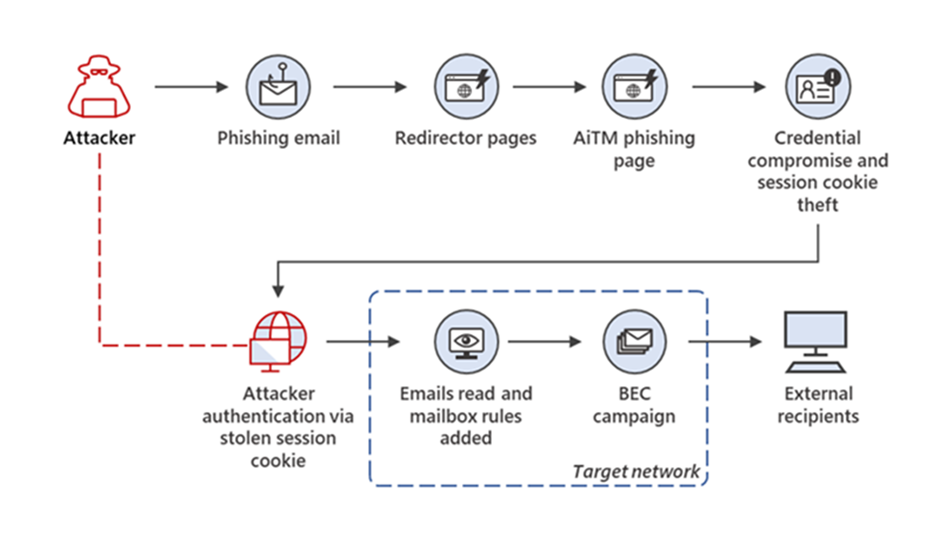
Researchers warn against massive AiTM (Adversary-in-the-Middle) attacks targeting enterprise users
Recently a large-scale phishing campaign was observed using adversary-in-the-middle (AitM) techniques to get around security protections and compromise enterprise email accounts. It was capable of bypassing multifactor authentication.
Prominent targets include fintech, lending, insurance, energy, manufacturing, and federal credit union verticals located in the U.S., U.K., New Zealand, and Australia.
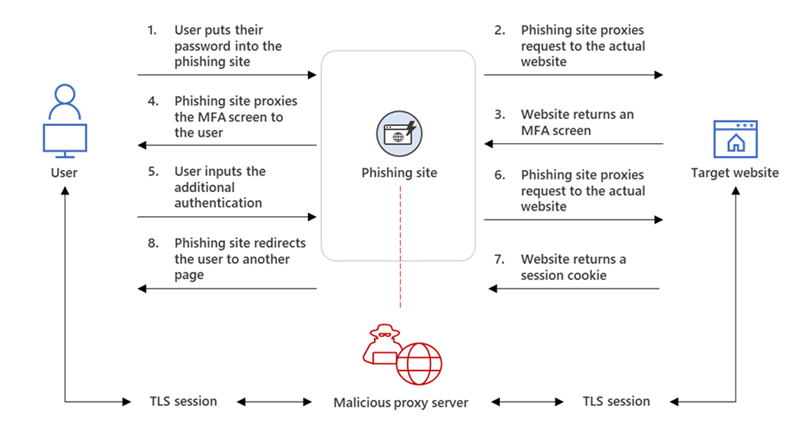
AiTM attacks complete the authentication process and captured the token. Currently, there are three main open-source AiTM phishing kits available that are widely known:
- Evilginx2
- Muraena
- Modlishka
All AiTMs work as a proxy between the victim and the target site. Every modern web service implements a session with a user after successful authentication so that re-authentication is not needed for every new page. The session functionality is part of the session cookie provided by the authentication services. The web server with the AiTM phishing kit proxies HTTP packets, based on this technique the website is identical to the original website. Only the URL is the only visible difference between the phishing site and the actual Microsoft sign-in site.
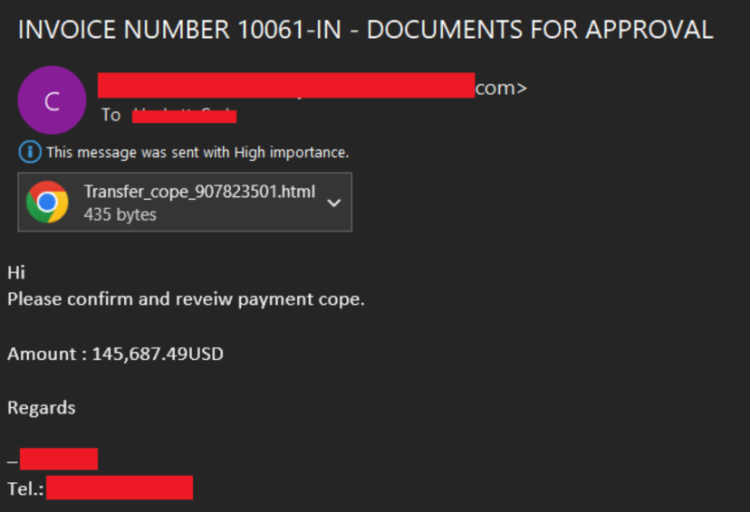
The ongoing campaign, effective June 2022, commences with an invoice-themed email sent to targets containing an HTML attachment, which includes a phishing URL embedded within it.

Upon opening the attachment via a web browser redirects the email recipient to the phishing page that masquerades as a login page for Microsoft Office, but not before fingerprinting the compromised machine to determine whether the victim is the intended target.
Fingerprinting-based evasion
This process happens immediately upon the page being visited. The initial page clients are served consists of JavaScript code, ripped from the FingerprintJS project, whose purpose is to collect information from the client’s browser to help the site determine if the person behind the browser is not an unsuspecting victim, but an unwelcome probing analyst or an automated bot.
The script gathers identifying information such as the client’s operating system, screen dimensions, and time zone, and communicates its findings back to the site by WebSocket traffic. The complete list of information gathered from the client’s machine is mentioned in the Appendix at the end of the blog.
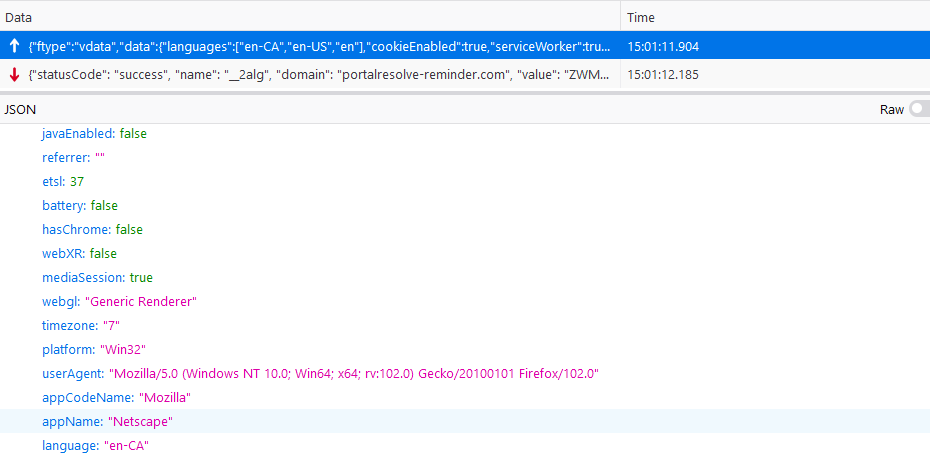
Client fingerprint data sent to the server over websocket.
With this information received, the site arrives at a verdict on whether it should continue reeling in the client, or should get rid of it by redirecting to the Google homepage.
Protect against AiTM phishing
With the growing enablement/adoption of MFA it is expected that AiTM phishing is growing in the upcoming next years (attackers using new techniques). Protecting against AiTM phishing is important.
Protecting is possible based on various configurations:
- Enable conditional access policies: Conditional access policies are evaluated and enforced every time an attacker attempts to use a stolen session cookie. Organizations can protect themselves from attacks that leverage stolen credentials by enabling policies such as compliant devices or trusted IP address requirements.
- Invest in advanced anti-phishing solutions: that monitor and scan incoming emails and visited websites. For example, organizations can leverage web browsers that can automatically identify and block malicious websites, including those used in this phishing campaign.
- Continuously monitor for suspicious or anomalous activities:
- Hunt for sign-in attempts with suspicious characteristics (for example, location, ISP, user agent, use of anonymizer services).
- Hunt for unusual mailbox activities such as the creation of Inbox rules with suspicious purposes or unusual amounts of mail item access events by untrusted IP addresses or devices.
Part of Microsoft 365 Defender is additional protection against AiTM phishing:
Based on threat data, the AiTM phishing campaign attempted to target more than 10,000 organizations since September 2021.
The defender uses cross-signal capabilities for detecting stolen session cookies. The alert with the name; Stolen session cookie was used is generated during the following situation; Cookie stolen using Microsoft Edge browser and attacker attempts to reply to the stolen session cookie to access Exchange Online.
AiTM phishing campaign and follow-on business email compromise (BEC) in the context of Microsoft 365 Defender threat data.
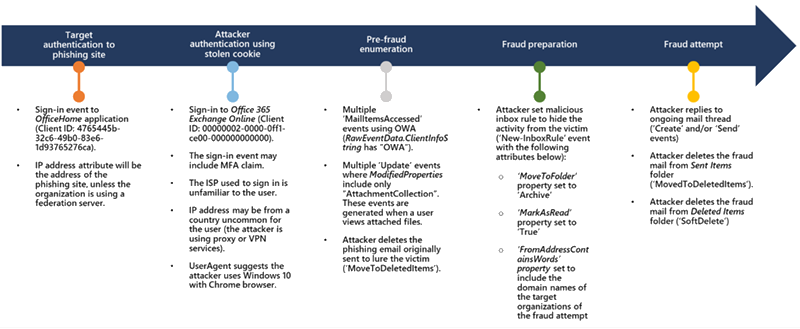
The following alerts are important in detecting AiTM phishing:
- Microsoft 365 Defender
- A stolen session cookie was used
- Defender for Cloud Apps
- Suspicious inbox manipulation rule
- Impossible travel activity
- Activity from infrequent country
- Azure AD Identity Protection
- Anomalous Token
- Unfamiliar sign-in properties
- Unfamiliar sign-in properties for session cookies
- Anonymous IP address
- Defender for Office 365
- Email messages containing malicious files removed after delivery
- Email messages from a campaign removed after delivery
- Creation of forwarding/redirect rule
- Defender for Endpoint
- Potential phishing website
- Implementing the Multi-factor Authentication (MFA)
- In Multifactor Authentication, to verify the users are mended to provide more than one verifiable information. This makes the process of authentication more secure. The goal of MFA is to create a layered defense that makes it more difficult for an unauthorized person to access a target, such as a physical location, computing device, network, or database.



