Unveiling the Threat – New Cosmic Energy Malware Emerges, Impacting Operational Technology
A new piece of malware, dubbed COSMICENERGY, has been discovered that targets industrial control systems (ICS). The malware is capable of exploiting vulnerabilities in ICS protocols to gain access to and control critical infrastructure systems.
Named Cosmic Energy, the latest malware family targeting operational technology (OT) is designed to interact with IEC 60870-5-104 (IEC-104) devices, sending remote commands to tamper with the actuation of power line switches and circuit breakers in an effort to cause power disruption. Mandiant believes it “poses a plausible threat to affected electric grid assets”.
The malware has two main components: Light Work, which implements the IEC-104 protocol to modify the RTU state to on/off, and PieHop, which connects to a specified remote MSSQL server for uploading files and issuing remote commands to an RTU using LightWork.
The security firm pointed out that Cosmic Energy is not capable of obtaining the information needed to carry out an attack on its own. The attacker needs to manually collect IP addresses and credentials. In fact, Mandiant believes the malware may have been created by a contractor at Russian cybersecurity company Rostelecom-Solar as part of a red teaming tool for power disruption and emergency response exercises. Rostelecom-Solar received a subsidy from the Russian government in 2019 to begin training cybersecurity experts and conducting such exercises. The malware may have been used in exercises conducted in 2021 or 2022.
The COSMICENERGY sample analyzed by Mandiant was uploaded to a malware scanning service in December 2021 by someone from Russia. Specifically, the malware interacts with IEC 60870-5-104 (IEC-104) devices, such as remote terminal units (RTUs), that are sometimes used in European, Middle Eastern, and Asian power transmission and distribution systems said the company. The malware has been found to contain modules that can exploit vulnerabilities in the IEC 60870-5-104 protocol, which is a widely used protocol for communication between ICS devices.
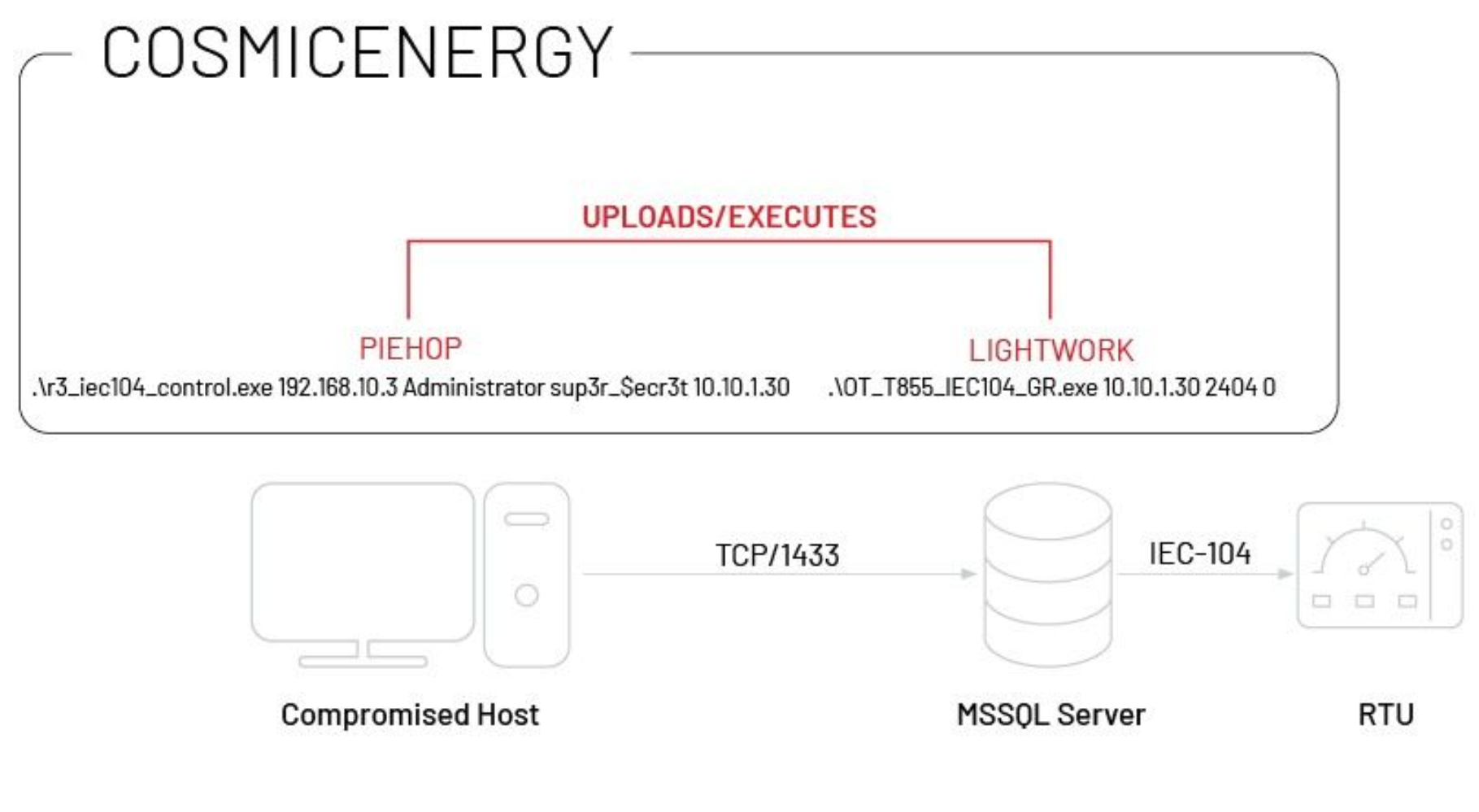
COSMICENERGY Execution Chain
The COSMICENERGY malware represents a new breed of cyber threats designed explicitly to exploit vulnerabilities within industrial control systems. These systems are responsible for managing and controlling various aspects of critical infrastructure, including power grids. The malware infiltrates the ICS network and aims to disrupt or sabotage the power grid’s operation by exploiting vulnerabilities within the protocols used to communicate between different components of the system.
Once COSMICENERGY has gained access to an ICS system, it can be used to issue commands to devices, such as power line switches and circuit breakers. This could potentially be used to cause power outages or other disruptions to critical infrastructure.
COSMICENERGY is the latest in a series of malware threats that have been designed to target ICS systems. In recent years, there have been a number of high-profile attacks on ICS systems, including the Stuxnet attack on Iran’s nuclear program and the Not Petya attack that caused widespread disruption in Ukraine.
The threat posed by COSMICENERGY and other ICS malware is a serious one. ICS systems are critical to the operation of many critical infrastructure systems, such as power grids, water treatment plants, and transportation systems. A successful attack on an ICS system could have a devastating impact on the economy and public safety.
Organizations that operate ICS systems need to take steps to protect themselves from these threats. This includes implementing security measures, such as firewalls, intrusion detection systems, and access control, as well as training employees on how to identify and report suspicious activity.
How to Protect Yourself from COSMICENERGY?
There are a number of steps that organizations can take to protect themselves from COSMICENERGY and other ICS malware threats. These include:
- Implementing security measures: Organizations should implement security measures, such as firewalls, intrusion detection systems, and access control, to protect their ICS systems from attack.
- Training employees: Employees should be trained on how to identify and report suspicious activity. This includes phishing emails, malicious websites, and unusual activity on ICS systems.
- Keeping systems up to date: Organizations should keep their ICS systems up to date with the latest security patches. This will help to protect them from known vulnerabilities that could be exploited by attackers.
- Monitoring systems: Organizations should monitor their ICS systems for suspicious activity. This includes looking for unusual network traffic, changes in system settings, and unauthorized access attempts.
- Security Assessments: Assessing the security vulnerabilities in an Industrial Control System (ICS) environment is crucial for maintaining the integrity and reliability of critical infrastructure. By choosing our organization for ICS security assessments, organizations can benefit from our expertise, experience, and dedication to help them protect their critical infrastructure from potential threats.
By taking these steps, organizations can help to protect themselves from the threats posed by COSMICENERGY and other ICS malware threats.



