“PhantomBlu” Cyber attackers Exploit Microsoft Office Users through OLE Vulnerabilities
In a cyberattack operation “PhantomBlu,” hundreds no of employees across various US-based organizations were targeted with phishing emails masquerading as messages from an accounting service.
This campaign represents a significant evolution in the tactics, techniques, and procedures (TTPs) employed by cyber criminals. Perhaps part of the trouble has to do with its sheer variety of tactics, techniques, and procedures (TTPs) it uses.
They are leveraging social engineering and advanced evasion techniques to deploy malicious code.
Attack: Monthly Salary Reports
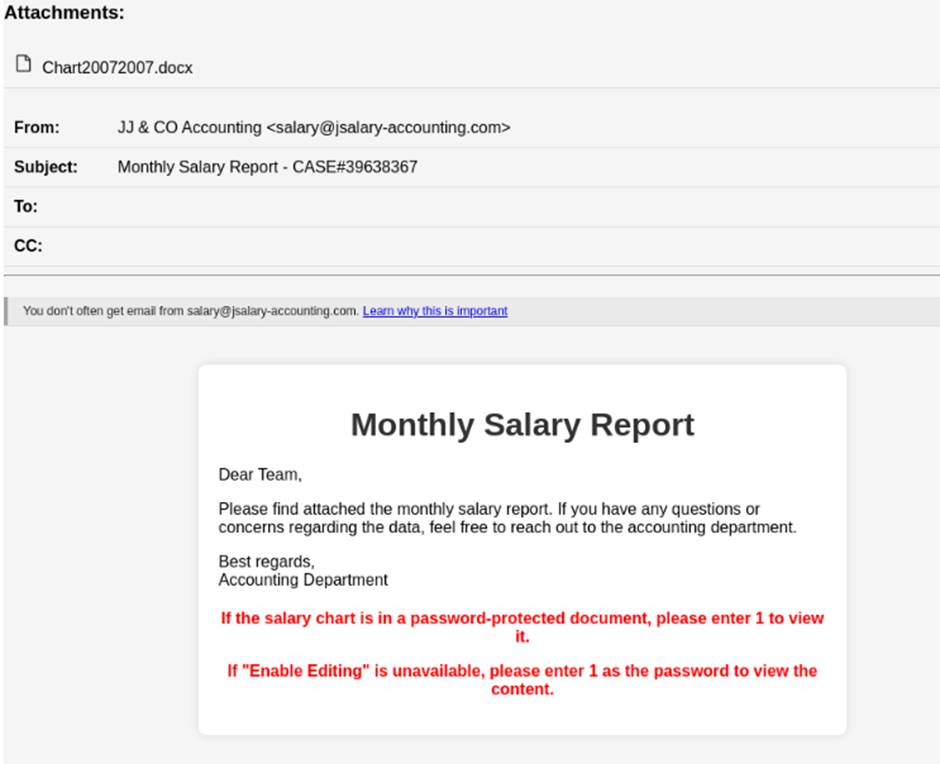
The attackers meticulously crafted email messages that appeared to originate from a legitimate accounting service. They instructed recipients to download an attached Office Word document (.docx) purportedly containing their “monthly salary report.”
The emails included detailed instructions for accessing the password-protected document, exploiting human curiosity and trust to initiate the attack chain.
Decoding PhantomBlu: Advanced Evasion In Action
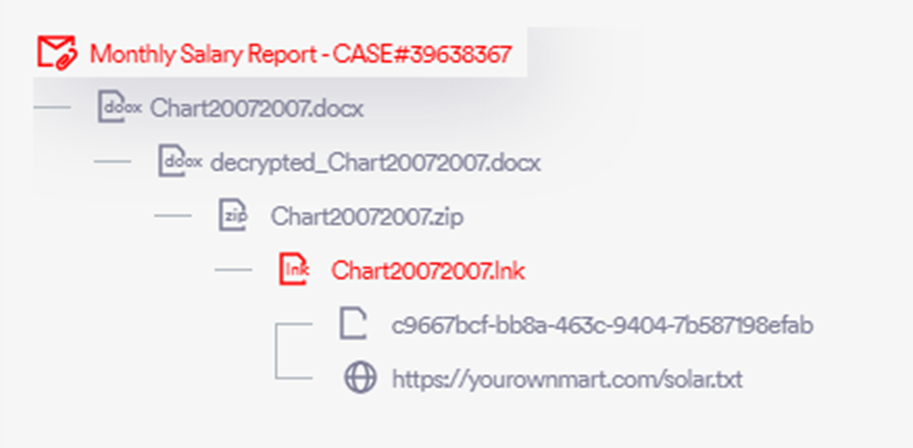
The PhantomBlu campaign utilized a technique known as OLE template manipulation (Defense Evasion – T1221), marking the first recorded instance of this TTP being used to deliver the NetSupport RAT (Remote Access Trojan) via email.
This method exploits document templates to execute malicious code without detection, bypassing traditional security measures by hiding the payload outside the document, which only executes upon user interaction.
Perception Point security researchers have recently identified a newly surfaced campaign targeting US-based organizations.
Dubbed “PhantomBlu,” the emerging malware campaign employs new TTPs and behaviors to evade detection and deploy the notorious [NetSupport RAT].
Dissecting The Malware: From Lure To Control
A forensic analysis of the LNK file revealed it as a PowerShell dropper designed to retrieve and execute a script from a specified URL. The script was heavily obfuscated to conceal its true intentions, which included downloading a secondary ZIP file, unpacking it, and executing the NetSupport RAT.
Further investigation into the secondary URL used by the attackers revealed a user-agent gated payload delivery, which was bypassed to obtain the payload, mirroring the attackers’ approach. The secondary PowerShell script’s execution resulted in the deployment of the NetSupport RAT.
How to safe from this types of Attack.
Emails have occupied a prominent place in modern business communication. They have become the most widely adopted dissemination channels today and are acting as legal documents in any formal environment, with low cost. Every organization from IT and BPO to health, insurance, and hospitality is making use of emails.
Ways to Reduce Email Based Threats
Emails always remain the weakest links to carry out cyberattacks. Following are some ways that can help you in reducing the email-based cyberattacks considerable.
1. Use Protected Emails with End-to-End Encryption
End-to-end encryption is a technology that encrypts all data before it is sent to a server, using an encryption key that the server does not possess. Encryption helps in protecting your mails against data leaks when there is a breach at the server level.
2. Do not Download Suspicious Email Attachments
Restrict downloading PDFs, Word documents, ZIP files that come attached from suspicious sources by blocking the access to such sources. Downloading such documents is nothing but letting in intruders.
3. Educate your employees
Hackers create malicious emails and make them look harmless using several social engineering, phishing and URL spoofing techniques. These malicious emails come with infected attachments and links, which when downloaded or clicked can lead to worst security compromises.



