AndroxGh0st Malware Targets Laravel Apps to Steal Cloud Credentials
Cybersecurity researchers have pinpointed a tool dubbed AndroxGh0st, specifically designed to target Laravel applications with the aim of extracting critical data. Employing an array of methodologies, AndroxGh0st undertakes tasks such as scanning .env files and capitalizing on vulnerabilities within cloud-based platforms such as AWS and Twilio. Its multifaceted approach enables it to infiltrate systems and access sensitive information. This poses a significant threat to the security and integrity of data stored within Laravel environments. Given its ability to exploit weaknesses in cloud-based applications, AndroxGh0st represents a formidable challenge for cybersecurity professionals. Efforts to defend against such attacks must include comprehensive security measures tailored to the unique risks posed by this sophisticated malware. As the landscape of cybersecurity threats continues to evolve, it is imperative to remain vigilant and proactive in implementing robust defenses. Collaboration among researchers, industry stakeholders, and cybersecurity professionals is essential in identifying emerging threats and developing effective countermeasures. By staying informed and adopting a proactive stance, organizations can mitigate the risks posed by AndroxGh0st and safeguard their Laravel applications against potential data breaches.
Functionality
AndroxGh0st, categorized as an SMTP cracker, operates by exploiting SMTP protocols through various tactics, including credential exploitation, web shell deployment, and vulnerability scanning. This malware strain has been in circulation since at least 2022, demonstrating a consistent presence within the threat landscape. Its primary objective revolves around infiltrating Laravel environment files to extract sensitive data, particularly credentials associated with cloud-based services. The modus operandi of AndroxGh0st underscores its sophisticated nature, posing significant challenges to cybersecurity efforts. By focusing on Laravel applications and cloud service credentials, AndroxGh0st exhibits a targeted approach, potentially causing extensive damage and compromising organizational security. As organizations strive to fortify their defenses against evolving cyber threats, understanding the nuances of AndroxGh0st is crucial for implementing effective countermeasures. Collaboration and information sharing among cybersecurity professionals play a pivotal role in enhancing collective resilience against this persistent menace. Through proactive measures and continuous vigilance, organizations can mitigate the risks posed by AndroxGh0st and safeguard their digital assets from exploitation.
Attack Chains
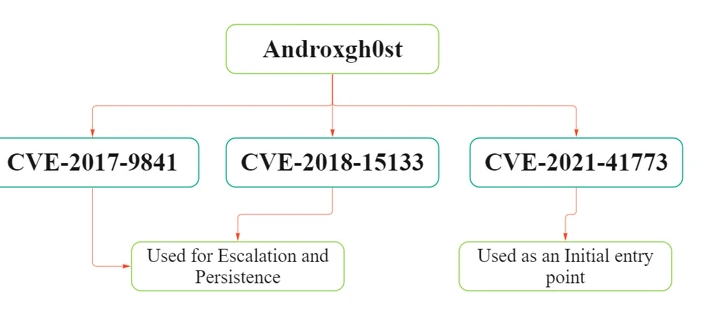
Exploiting identified vulnerabilities within the Apache HTTP Server, Laravel Framework, and PHPUnit, the malware maneuvers to secure initial access and elevate its privileges. These attack sequences strategically capitalize on weaknesses such as CVE-2021-41773, CVE-2017-9841, and CVE-2018-15133, enabling the establishment of enduring control over targeted systems. By exploiting these vulnerabilities, the malware effectively establishes persistence, allowing for prolonged access and manipulation of compromised systems. The utilization of CVEs highlights the malware’s sophisticated tactics in navigating through security defenses, posing significant challenges to cybersecurity efforts. As organizations grapple with the evolving threat landscape, addressing and patching these vulnerabilities become paramount in thwarting potential attacks. Proactive measures, including regular security assessments and timely patch deployments, are crucial in mitigating the risks associated with these exploit chains. Collaboration among cybersecurity professionals and industry stakeholders remains instrumental in fortifying defenses and staying ahead of emerging threats. Through concerted efforts and continuous vigilance, organizations can enhance their resilience against malware exploits and safeguard critical assets from compromise.
Impact and Spread
Engineered for data exfiltration, AndroxGh0st is meticulously crafted to extract sensitive information from diverse repositories, encompassing .env files, databases, and cloud credentials. This broad spectrum of targeted sources furnishes threat actors with a trove of valuable data, facilitating the deployment of supplementary payloads onto compromised systems. Recent monitoring activities have detected a surge in exploiting CVE-2017-9841, underscoring the imperative for swift updates and patches. The escalation in exploiting this vulnerability accentuates the urgency for organizations to remain vigilant and proactive in addressing security vulnerabilities. Timely updates and proactive mitigation strategies are paramount in mitigating the risks posed by AndroxGh0st and curtailing its impact on organizational security. Collaborative efforts among cybersecurity practitioners and stakeholders play a pivotal role in fortifying defenses and minimizing the potential fallout from such threats. By embracing a proactive security posture and prioritizing prompt updates, organizations can enhance their resilience against AndroxGh0st and similar malicious actors in the evolving cybersecurity landscape.
Geographical Distribution
Detection of attack attempts leveraging AndroxGh0st has been widespread, spanning across multiple nations, including the United States, United Kingdom, China, the Netherlands, Germany, Bulgaria, Kuwait, Russia, Estonia, and India. These global detections underscore the pervasive nature of the threat posed by AndroxGh0st, transcending geographical boundaries. The broad geographical distribution of attack attempts highlights the indiscriminate targeting of AndroxGh0st, demonstrating its potential impact on organizations worldwide. Organizations across various regions must remain vigilant and implement robust cybersecurity measures to mitigate the risks associated with AndroxGh0st and similar threats. Collaborative efforts on a global scale are essential in addressing the evolving cybersecurity landscape and combating the proliferation of sophisticated malware like AndroxGh0st. By fostering cooperation and information sharing, cybersecurity stakeholders can enhance collective resilience and effectively mitigate the impact of malicious cyber activities.
Related Developments
In addition to AndroxGh0st, recent cybersecurity developments have unveiled attacks targeting vulnerable WebLogic servers located in South Korea. These servers have been exploited to distribute various malicious tools, including z0Miner and fast reverse proxy (FRP). Furthermore, malicious campaigns have been identified targeting AWS instances, deploying binaries linked to decentralized content delivery networks such as Meson Network. These emerging threats underscore the diversification of attack vectors and the sophistication of cyber adversaries. The exploitation of WebLogic servers highlights the ongoing challenges posed by unpatched vulnerabilities in critical infrastructure. Similarly, the deployment of malicious binaries on AWS instances underscores the evolving tactics employed by threat actors to compromise cloud environments. It is imperative for organizations to remain vigilant and adopt proactive security measures to mitigate the risks associated with these emerging threats. Collaboration among cybersecurity professionals and industry stakeholders is essential in developing effective strategies to defend against evolving cyber threats. By staying informed and proactive, organizations can enhance their resilience and protect against the ever-changing threat landscape.
Emerging Threats
The utilization of Meson Network for cryptocurrency mining illuminates the evolving strategies employed by threat actors in the cyber landscape. Although legitimate services such as Meson Network are established, malicious entities continuously innovate to exploit cloud infrastructures for monetary purposes. This dynamic underscores the persistent efforts of attackers to capitalize on emerging technologies and platforms. While legitimate users engage with Meson Network for its intended purposes, cyber adversaries exploit its infrastructure for illicit cryptocurrency mining activities. The prevalence of such tactics highlights the need for robust cybersecurity measures to safeguard cloud environments from exploitation. As attackers adapt and refine their methods, organizations must remain vigilant and proactive in defending against emerging threats. Collaborative efforts among cybersecurity professionals and industry stakeholders are crucial in identifying and mitigating the risks associated with malicious exploitation of cloud resources. By staying informed and implementing proactive defenses, organizations can fortify their resilience against evolving cyber threats in the cloud environment.
Recommendations
- Patch Management: Regularly update and patch vulnerable software components, including Apache HTTP Server, Laravel Framework, and PHPUnit. Addressing known vulnerabilities, such as CVE-2021-41773, CVE-2017-9841, and CVE-2018-15133, is critical to prevent initial access and privilege escalation by AndroxGh0st.
- Environment Hardening: Implement robust security measures to harden your environment against potential attacks. Configure firewalls, intrusion detection systems (IDS), and access controls to restrict unauthorized access. Utilize secure coding practices to minimize the exploitation of software vulnerabilities.
- Secure Configuration: Ensure that sensitive information, such as AWS and Twilio credentials stored in .env files, are adequately protected. Encrypt sensitive data at rest and in transit using strong encryption algorithms. Implement multi-factor authentication (MFA) and role-based access controls (RBAC) to limit the exposure of privileged credentials.
- Threat Monitoring and Detection: Deploy advanced threat detection solutions to monitor for suspicious activities and indicators of compromise (IOCs). Utilize intrusion detection and prevention systems (IDPS) to detect and block malicious traffic associated with AndroxGh0st. Implement comprehensive logging and auditing mechanisms to facilitate timely incident response.
- Incident Response Planning: Develop and regularly update an incident response plan to effectively mitigate and respond to security incidents involving AndroxGh0st. Define clear roles and responsibilities for incident response team members and establish communication channels for reporting and escalating security incidents promptly.



