GitHub Account Hijacking in Supply Chain Attack: Impact on Top.gg and Other Targets
A recent discovery has unveiled a highly sophisticated software supply chain attack, targeting both individual developers and the GitHub organization account linked with Top.gg, a prominent platform for Discord bot discovery. Orchestrated by unidentified adversaries, this attack employed a multitude of techniques with the primary goal of compromising developer accounts and injecting malicious code into widely used packages. The attackers exploited the inherent trust within the open-source community to perpetrate their malicious activities. By compromising legitimate accounts and repositories, they were able to distribute trojanized versions of popular Python packages, thereby compromising the integrity of software dependencies relied upon by countless users. This malicious campaign underscores the evolving threat landscape faced by the open-source ecosystem, highlighting the critical need for robust security measures and heightened vigilance among developers and organizations. As the attack demonstrates, even trusted platforms like GitHub and PyPI are susceptible to infiltration by malicious actors, emphasizing the importance of continuous monitoring and proactive defense strategies. In response to this incident, it’s imperative for the community to prioritize security practices, such as thorough vetting of dependencies and prompt detection of anomalous activities within repositories. Ultimately, by fostering a culture of security awareness and collaboration, the open-source community can better defend against future threats and safeguard the integrity of software supply chains.
Attack Techniques Utilized:
The attackers employed a variety of tactics, techniques, and procedures (TTPs) to carry out the attack:
- Account Takeover via Stolen Browser Cookies: The perpetrators seized control of legitimate accounts, including the verified GitHub account of “editor-syntax,” through the illicit acquisition of session cookies. By pilfering these cookies, they effectively bypassed authentication measures, enabling unauthorized access without the necessity of knowing account passwords.
- Malicious Code Injection: The attackers infiltrated repositories by injecting malicious code, which included tampered versions of popular Python packages like Colorama. These altered codes harbored malicious payloads and were strategically hosted on a typosquatted domain, masquerading as the legitimate PyPI repository. This duplicitous maneuver aimed to deceive users into incorporating compromised packages, thereby facilitating the propagation of the malicious elements.
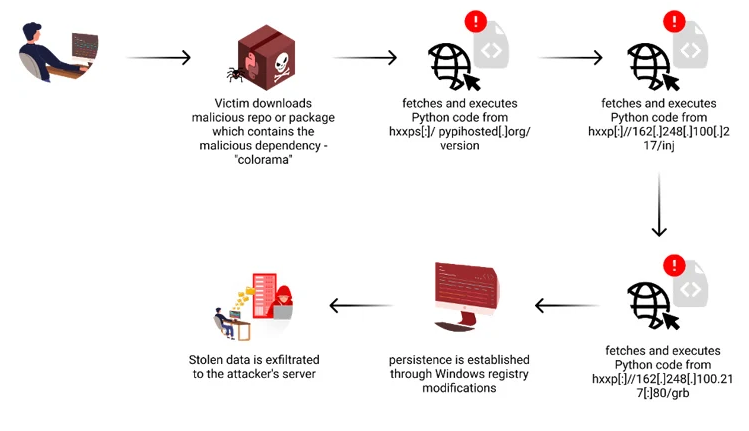
- Setting up a Custom Python Mirror: In a further escalation of their tactics, the assailants erected a counterfeit mirror of the official PyPI repository. Through this fake mirror, they disseminated fraudulent packages, such as “yocolor,” which acted as carriers for the malware-infected “colorama” package. By employing this deceptive tactic, they exploited the trust placed in the PyPI ecosystem, thereby amplifying the reach of their malicious payload.
- Publication of Malicious Packages to PyPI: Exploiting the inherent trust in the open-source package ecosystem, the threat actors uploaded counterfeit packages directly to the PyPI repository. These deceitful packages, laden with malware, were distributed under the guise of legitimate software libraries. This method of distribution allowed the attackers to exploit the unsuspecting users who rely on PyPI for sourcing their software dependencies, further amplifying the reach and impact of their malicious campaign.
Propagation Mechanisms
The malicious packages and code alterations were disseminated through various channels, including:
- Inclusion of Malicious Packages in “requirements.txt” Files: The attackers modified “requirements.txt” files within GitHub repositories to include the malicious packages as dependencies. By doing so, unsuspecting developers who installed dependencies using the standard package manager, such as pip, inadvertently introduced the malicious code into their projects.
- Obfuscation through Multiple Changes in Single Commit: To obfuscate their activities and hinder detection efforts, the threat actors bundled multiple changes into a single commit within rogue repositories. This tactic aimed to camouflage alterations made to the repositories, making it more challenging for security analysts to identify and mitigate the presence of malicious code.
- Utilization of Anonymous File-Sharing Services: In an effort to transfer stolen data to their infrastructure covertly, the attackers leveraged anonymous file-sharing services like GoFile and Anonfiles. By utilizing these platforms, they evaded traditional detection methods, allowing for the surreptitious transfer of sensitive information such as stolen credentials, passwords, and other valuable data.
Malware Functionality
The malware embedded in the counterfeit packages facilitated a multi-stage infection process, enabling the execution of Python code from remote servers. Key functionalities of the malware include:
- Establishment of Persistence via Windows Registry Manipulation: The attackers ensured the persistence of their malware on infected hosts by making changes to the Windows Registry. This tactic allowed the malicious code to remain active even after system reboots, providing sustained access to compromised machines for continued nefarious activities.
- Exfiltration of Data from Various Sources: The malware facilitated the theft of sensitive data from a range of sources, including web browsers, cryptocurrency wallets, and messaging platforms such as Discord, Instagram, and Telegram. By accessing and extracting information from these platforms, the attackers could potentially acquire valuable user credentials, personal information, and cryptocurrency assets.
- Targeted File Theft Mechanism: The malware included a component specifically designed to steal files from predefined directories on infected systems. By targeting directories commonly used for storing important documents and sensitive data, such as the Desktop, Downloads, Documents, and Recent Files folders, the attackers aimed to obtain additional information that could be valuable for their malicious objectives. Subsequently, the captured data was transferred to the attackers’ infrastructure for further exploitation or monetization.
Mitigation Strategies
To mitigate the risk of similar attacks, it is imperative to adopt proactive security measures:
- Vigilance when installing packages and repositories, even from trusted sources.
- Thorough vetting of dependencies to identify and mitigate potential security risks.
- Monitoring for suspicious network activity and anomalous behavior within repositories.
- Maintenance of robust security practices, including regular updates, patch management, and employee training on security awareness



