UNC3886 Exploits Zero-Day (CVE-2023-20867) Flaw in VMware ESXi Hosts: A Closer Look
The Chinese state-sponsored group known as UNC3886 has once again made headlines with its advanced cyber espionage operations. This highly adept threat actor has recently been discovered exploiting a zero-day vulnerability in VMware ESXi hosts, enabling them to infiltrate and backdoor Windows and Linux systems. In this blog, we delve into the details of this concerning development and shed light on UNC3886’s modus operandi.
VMware Tools Authentication Bypass Vulnerability:
One of the critical vulnerabilities leveraged by UNC3886 is the VMware Tools authentication bypass flaw, designated as CVE-2023-20867. This flaw allows the execution of privileged commands on Windows, Linux, and PhotonOS (vCenter) guest virtual machines without requiring authentication of guest credentials from a compromised ESXi host. To make matters worse, the default logging on guest VMs fails to capture any trace of this malicious activity.
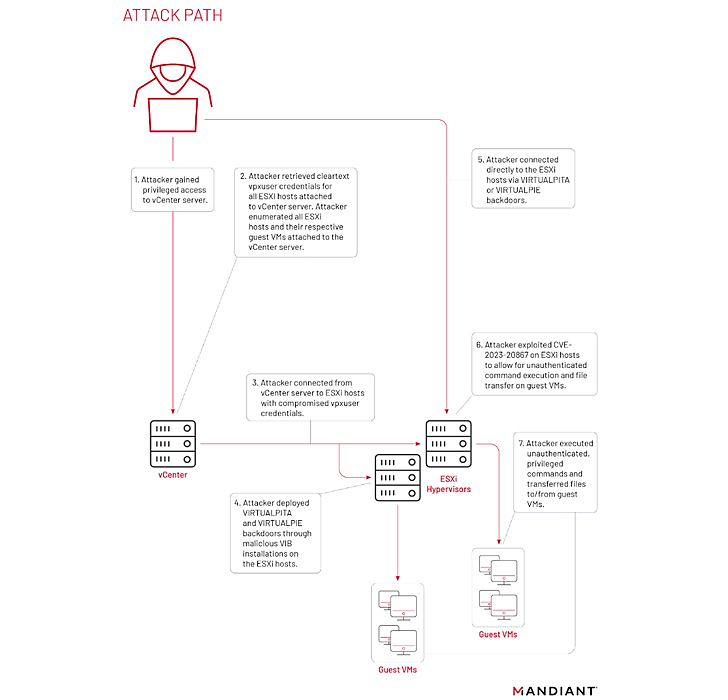
In their endeavors to exploit ESXi systems, the threat actor has demonstrated a multi-faceted approach. They have been observed gathering login credentials from vCenter servers while also exploiting CVE-2023-20867 to execute commands and transfer files to and from guest virtual machines via compromised ESXi hosts.
UNC3886’s operational tactics exhibit a notable utilization of Virtual Machine Communication Interface (VMCI) sockets, enabling lateral movement and persistent access. This technique establishes a concealed communication channel between the ESXi host and its guest VMs, allowing for covert interactions. By leveraging this open channel, the threat actor can achieve renewed persistence on a compromised ESXi host as long as a backdoor is deployed and the attacker gains initial access to any guest machine.
Furthermore, the recent findings coincide with the disclosure made by a Threat researcher and identified three distinct vulnerabilities (CVE-2023-20887, CVE-2023-20888, and CVE-2023-20889) in VMware Aria Operations for Networks, posing the risk of remote code execution.
Uncovering UNC3886, Threat Group
UNC3886, a cyber threat group known for targeting defense, technology, and telecommunication organizations, has been identified using sophisticated techniques to compromise vCenter servers. They employed scripts to extract login credentials from the connected vPostgreSQL database, allowing them to gain unauthorized access to ESXi hosts and their guest virtual machines. By exploiting a specific vulnerability (CVE-2023-20867), they executed commands and transferred files between compromised ESXi hosts and guest VMs without leaving any authentication traces. The group also utilized two backdoors (VirtualPita and VirtualGate) for lateral movement, leveraging VMCI sockets. These tactics grant the attackers persistent access, enable network segmentation bypass, and allow unauthenticated actions with privileged accounts across virtual machines. Their exploitation of zero-day bugs in firewall and virtualization solutions adds to the group’s capabilities and poses a significant threat to targeted organizations.
UNC3886’s Backdoor Techniques:
UNC3886 first caught the attention of the cybersecurity community when it was discovered by a Google-owned threat intelligence firm in September 2022. The group was found infecting VMware ESXi and vCenter servers with backdoors named VIRTUALPITA and VIRTUALPIE. These backdoors enable persistent access and provide UNC3886 with a foothold to conduct their covert operations.
Exploiting Medium-Severity Flaw in Fortinet FortiOS:
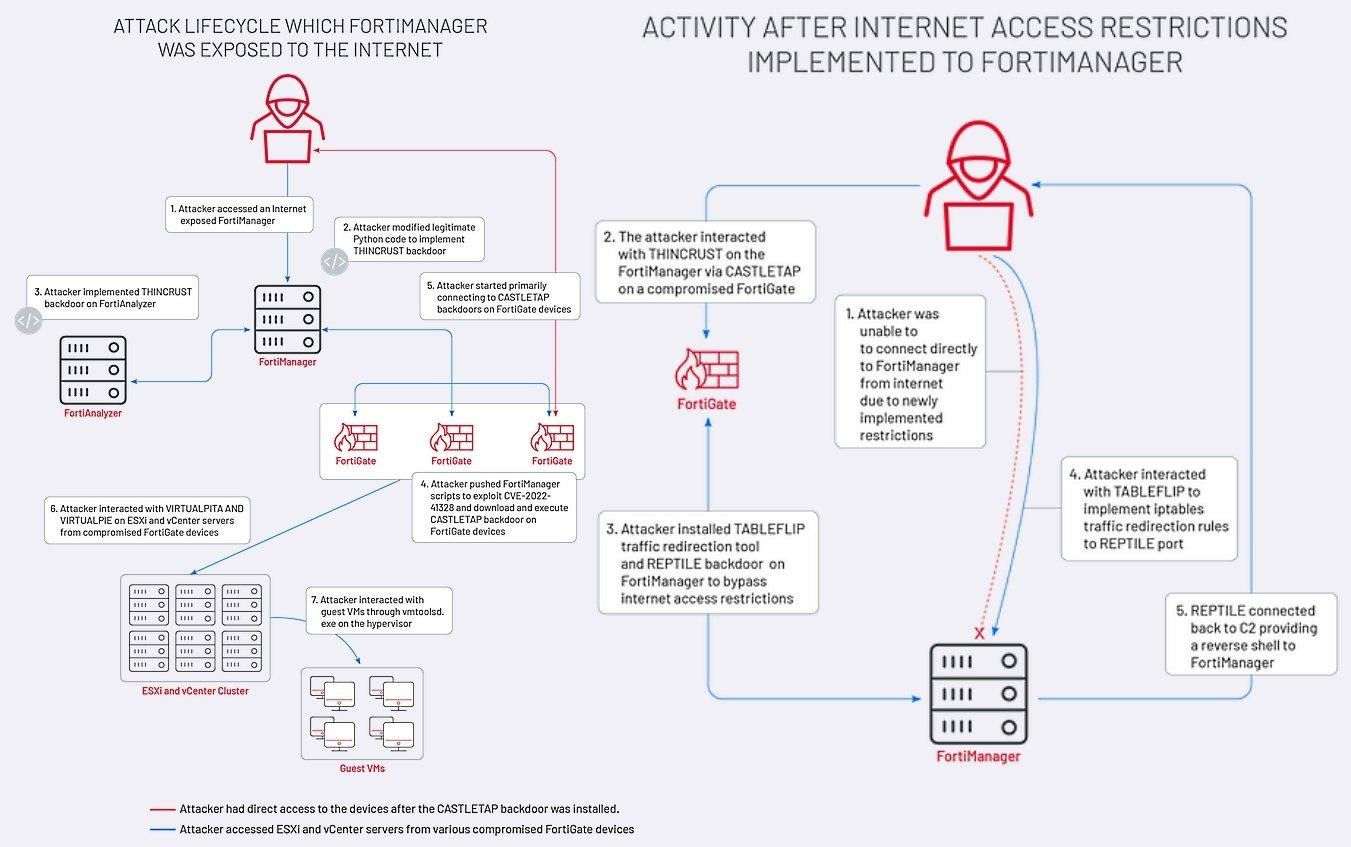
In March of this year, UNC3886 was also implicated in the exploitation of a medium-severity security flaw in the Fortinet FortiOS operating system. This allowed them to deploy implants on network appliances and establish communication with their previously mentioned malware. The group’s ability to exploit multiple vulnerabilities demonstrates their technical prowess and highlights the sophistication of their tactics.
UNC3886’s Targets and Methodology:
Defense, technology, and telecommunication organizations in the United States, Japan, and the Asia-Pacific region have become prime targets for UNC3886. The group’s access to extensive research and technical support enables them to exploit the underlying technology of the appliances they target. Their strategy often involves weaponizing flaws in firewall and virtualization software, effectively evading EDR (Endpoint Detection and Response) solutions.
“UNC3886 continues to present challenges to investigators by disabling and tampering with logging services, selectively removing log events related to their activity,” it further added. “The threat actors’ retroactive cleanup performed within days of past public disclosures on their activity indicates how vigilant they are.”
Remediation:
UNC3886’s exploitation of a zero-day flaw in VMware ESXi hosts serves as a stark reminder of the ever-present cyber threats faced by organizations worldwide. Their advanced techniques and targeted attacks underscore the need for heightened vigilance and robust security measures. It is crucial for enterprises to stay informed about emerging threats and employ comprehensive cybersecurity strategies to protect their valuable assets from such sophisticated adversaries by following remediation steps to mitigate Zero day Exploitation
- Keep Software Up-to-Date: Regularly update VMware ESXi hosts, vCenter servers, and associated tools to ensure that security patches and fixes are applied promptly. This includes VMware Tools, which should be updated across guest virtual machines as well.
- Implement Strong Access Controls: Employ robust access controls and least privilege principles to limit administrative privileges on ESXi hosts, vCenter servers, and guest virtual machines. Regularly review and audit user accounts to ensure that only authorized individuals have elevated access.
- Enable Logging and Monitoring: Enable comprehensive logging and monitoring across ESXi hosts, vCenter servers, and guest virtual machines. This includes enabling and reviewing logs for authentication attempts, command executions, and file transfers to detect any suspicious activity.
- Apply Network Segmentation: Implement network segmentation to isolate critical infrastructure components, such as ESXi hosts, vCenter servers, and guest virtual machines. This helps contain potential compromises and limits lateral movement in case of a breach.
- Utilize Intrusion Detection/Prevention Systems: Deploy and configure intrusion detection and prevention systems (IDPS) to monitor network traffic and detect any signs of UNC3886’s activities. Regularly update the IDPS signatures to detect new attack patterns and malware associated with the threat group.
- Implement Endpoint Protection: Deploy robust endpoint protection solutions, including advanced antivirus and endpoint detection and response (EDR) systems. These solutions can help detect and mitigate UNC3886’s malware and suspicious activities on ESXi hosts, vCenter servers, and guest virtual machines.
- Establish an Incident Response Plan: Develop and regularly update an incident response plan that outlines the steps to be taken in the event of a security incident or potential compromise. This plan should include procedures for isolating affected systems, notifying relevant stakeholders, and engaging with incident response experts if necessary.
- Engage with Threat Intelligence: Stay informed about the latest threat intelligence reports and updates related to UNC3886 and similar threat actors. This information can help organizations proactively adapt their security strategies and defenses to mitigate the evolving threat landscape.



